Cyber-espionage group, Suckfly targeted Indian organisations: Symantec

Symantec says that Suckfly conducted campaigns against government and commercial organisations in India
Symantec has published a report on the activities of Suckfly, a cyber-espionage group. As per the report, the group conducted campaigns against a number of targets including government and commercial organisations in India. Symantec identified a number of attacks over a two-year period starting from April 2014. While these attacks occurred in several different countries, the company noted that the main targets were individuals and organizations primarily located in India.
Read the complete press release below
Today, Symantec published a blog on activities of Suckfly- an advance cyberespionage group that conducted long term espionage campaigns against high profile targets including government and commercial organizations in India. Symantec identified a number of attacks over a two-year period, beginning in April 2014. These attacks occurred in several different countries, but Symantec’s investigation revealed that the primary targets were individuals and organizations primarily located in India. The Indian targets show a greater amount of post-infection activity than targets in the other regions. This suggests that these attacks were part of a planned operation against specific targets in India. The Symantec blog on the activities of Suckfly takes an in-depth look at its activities in India along with its attack lifecycle. Listed below are the key findings of this research:
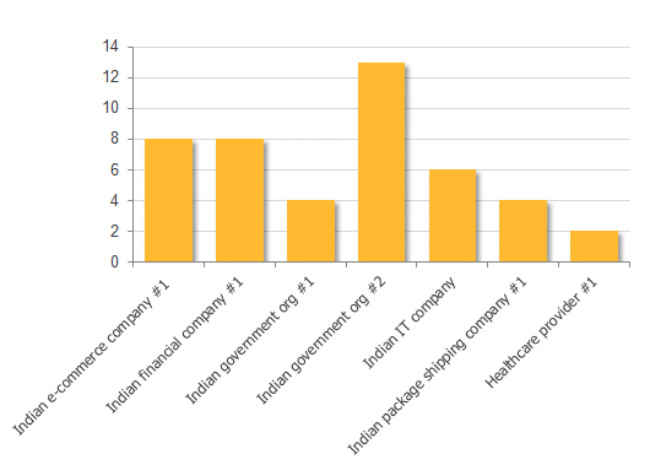
Many of the targets Symantec identified were well known commercial organizations located in India. These organizations included (Ref. Fig 1)
- One of India's largest financial organizations
- A large e-commerce company
- The e-commerce company's primary shipping vendor
- One of India's top five IT firms
- A United States health care provider's Indian business unit
- Two government organizations
Figure 1: The infection rate for each of the targets
Indian Government Organizations on Suckfly’s Radar
- Suckfly spent more time attacking the government networks compared to all but one of the commercial targets. Additionally, one of the two government organizations had the highest infection rate of the Indian targets.
- Indian government org #2 (Ref Fig 1) is linked to departments of India's central government and is responsible for implementing network software for different ministries and departments. The high infection rate for this target is likely because of the organization's access, technology, and information that it has on other Indian government organizations.
- Suckfly's attacks on government organizations that provide information technology services to other government branches is not limited to India. They have conducted attacks on similar organizations in Saudi Arabia, likely because of the access that those organizations have.
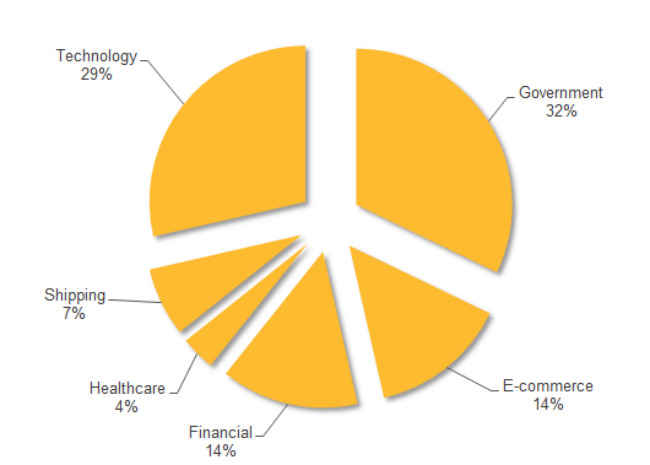
Figure 2: Suckfly victims, by industry
While most of Suckfly group's attacks are focused on government organisations (32%), technology (29%), e-commerce (14%), financial (14%), shipping (7%) and healthcare (4%) were also targeted by this group.
Suckfly Attack lifecycle
- One of the attacks Symantec investigated provided detailed insight into how Suckfly conducts their operations. In April 2015, Suckfly conducted a multistage attack conducted between April 22, 2015 and May 4, 2015 against an e-commerce organization based in India. Similar to their other attacks, Suckfly used the Nidiran backdoor along with a number of hack tools to infect the victim's internal hosts. The tools and malware used in this breach were also signed with stolen digital certificates. Read more about the Suckfly attack cycle on the blog.
Suckfly attempted to impact India’s Economy
- Suckfly targeted one of India’s largest e-commerce companies, a major Indian shipping company, one of the largest financial organizations, and an IT firm that provides support for India’s largest stock exchange. All of these targets are large corporations that play a major role in India’s economy. Attacking one of these organizations would be detrimental to that organization. By targeting all of these organizations together, Suckfly could have had a much larger impact on India and its economy.
- In Suckfly has the resources to develop malware, purchase infrastructure, and conduct targeted attacks for years while staying off the radar of security organizations. Symantec believes that Suckfly will continue to target organizations in India, and similar organizations in other countries to provide economic insight to the organization behind Suckfly's operations.
Insights on the Indian threat landscape from the Symantec Internet Security Threat Report (ISTR)
- In 2015, Symantec’s Internet Security threat Report (ISTR) had highlighted the rise in targeted attacks aimed at Indian businesses dealing with critical infrastructure.
- Further the latest edition of the report (ISTR 21) highlighted that Indian organizations were the 6th most targeted in Asia, with targeted organizations on the receiving end of two attacks on an average. 40 percent of BFSI businesses were also attacked at least once.
The nature of the Suckfly attacks suggests that it is unlikely that the threat group orchestrated these attacks on their own. Symantec believes that Suckfly will continue to target organizations in India, and similar organizations in other countries to provide economic insight to the organization behind Suckfly's operations.
Protection
Symantec has the following detections in place to protect against Suckfly’s malware:
Antivirus
- Backdoor.Nidiran
- Backdoor.Nidiran!g1
- Hacktool
- Exp.CVE-2014-6332
Intrusion prevention system
- Web Attack: Microsoft OleAut32 RCE CVE-2014-6332
- Web Attack: Microsoft OleAut32 RCE CVE-2014-6332 2
- Web Attack: Microsoft OleAut32 RCE CVE-2014-6332 4
- Web Attack: OLEAUT32 CVE-2014-6332 3
- System Infected: Trojan.Backdoor Activity 120