More than 200 Chrome extensions spy on you, says study

Research conducted by Precog, an IIIT Delhi research team, reveals privacy invasions by multiple browser extensions
A study by IIIT Delhi research team Precog claims that there are 218 browser extensions on the Chrome Web Store, out of the 43,000 that they checked, which are spying on their cumulative 3 million (approx) users. The study also explains the methods which these extensions employ and how these can be detected.
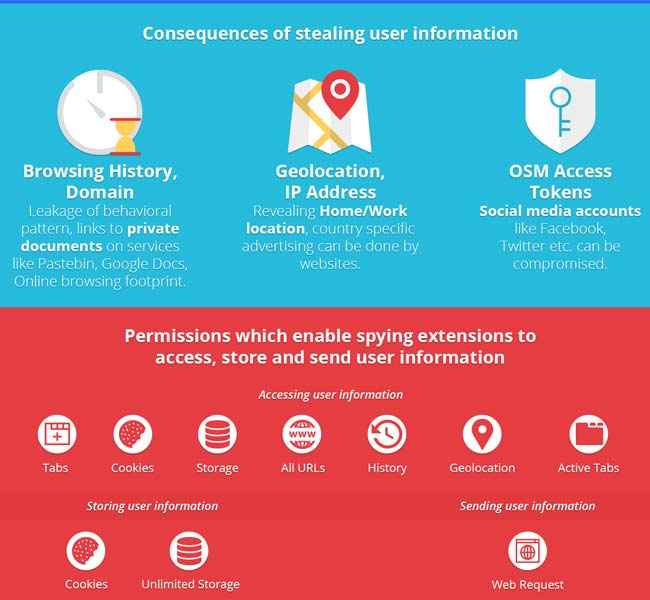
The problem of a browser extension spying on you is that it can pretty much detect, and consequently leak, anything that you do within the browser if it has the right permissions approved at install. Creating browser extensions is not a time or money extensive exercise which, on the other hand, gets access to a goldmine of personalised information that will be used for targeted advertising. The study claims that information like your browsing history, IP Address, Geolocation, Online Social Media (OSM) access tokens and domains visited are leaked by the extensions, with browsing history being the most in demand piece of information.
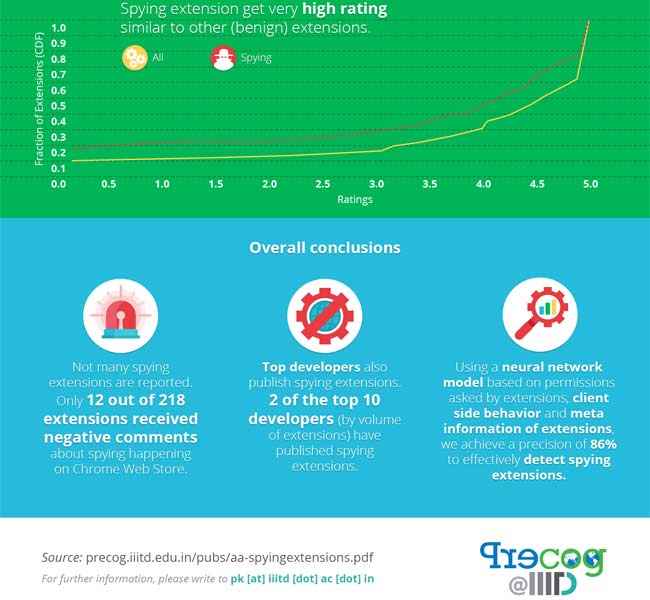
Another alarming statistic that is claimed by the study is that about 51% of the spying extensions have a rating of more than 4.0 on the Chrome Store. If this is an accurate number, it does show that users don’t generally check for the permissions that a browser extension is seeking at the time of installation.
What these browser extensions mainly seek to do, as revealed in the study, is to gain access to user info through various Chrome API calls that were approved earlier as permissions. One of the highest sought permission is something called ‘Tabs’, which, according to the study, is asked for by about 95% of the spying extensions as compared to an approx average of 53% across all the Chrome Store extensions they tested. This permission allows them to access the browser history and check the tabs currently open during the browser session.
The study also found that about 188 of the 218 extensions store information on the client side using ‘unlimited storage’ and ‘cookies’ permissions. The interesting bit is that many of these extensions obfuscate the data being sent, which can be viewed as a security measure but can also be with the intention of making it harder for a data leak to be detected.
We did reach out to the team for a full list of the detected extensions and specific evidence related to particular extensions, and we were informed that it will be shared pending peer review of the research paper. We shall be updating this article as soon as we receive that information.
The process that the research group has used involve semi-automated methods, and the research goes on to explain how the process can be fully automated using neural networks and machine learning. Such a process can be implemented in browsers to notify users when such an extension is being installed. And from the browser’s side, in this case, Chrome, there needs to be insistence towards developers to reveal the exact data that the extensions will access.
It wouldn’t be too inaccurate to say that technology and privacy invasion almost go hand in hand these days. There are multiple avenues through which your private information can be publicly compromised, or worse, land up in the hand of people with malicious intent. Take smartphone apps for example – while the tech savvy ones among us do notice which permissions are being asked for by each app we installed, it is still mostly an ignored thing at this day and age. While there is at least some awareness about smartphone apps when it comes to privacy invasion, there is little or no such awareness among the general populace about the same thing being perpetrated by browser extensions.
And Chrome doesn't exactly have a stellar record when it comes to respecting user privacy. It is guilty of multiple counts of user information tracking, as it has itself accepted at times and been caught by users some of the other times. These include but are maybe not limited to:
- Sharing filenames for downloaded files with Google.
- Connects to Google every 30 minutes to download a list of malicious URLs, hence lets Google know when you're using Chrome.
- Google account login transmits browsing tabs, history etc to servers.
- While you are typing a URL, it connects to that website in the background.
- An encrypted RLZ identifier that contains Chrome usage information in every query through Chrome URL address.
Hence, in the end, the most important step can only be taken by you, the user. Do not take the installation of browser extensions, or in fact any program or application on your computer, lightly even if you think you’re reasonably well protected. A little caution never harmed anyone, right? Go ahead and look into the permissions of such extensions that you are already using and make this a habit for the future.
You can read the blog of the research team announcing this result here and the full report here.
Image Courtesy: Precog, IIIT Delhi