Gooligan Android Malware compromises 1 million Google accounts: Report
Gooligan is active in 86 apps available in third-party marketplaces and sends data about the device

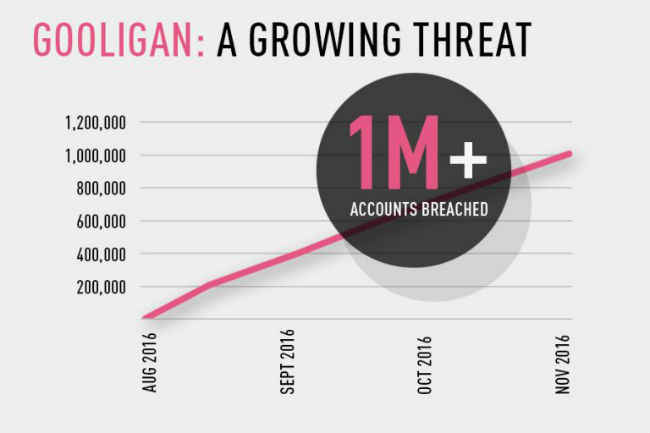
A new Android malware has reportedly compromised more than 1 million Google accounts. The new malware dubbed Gooligan has been found active in at least 86 apps and has affected hundred of accounts associated with enterprise users.
 Survey
SurveyAccording to researchers from security firm Check Point Software Technologies, Gooligan is active in 86 apps available in third-party marketplaces. Once installed, the malware uses rooting to gain access to system privileges on devices running Android 4.0 – right from Ice Cream Sandwich to KitKat and Android 5.0 Lollipop. Android 4.0 and Android 5.0 combined are running on nearly 73 percent of Android smartphones.
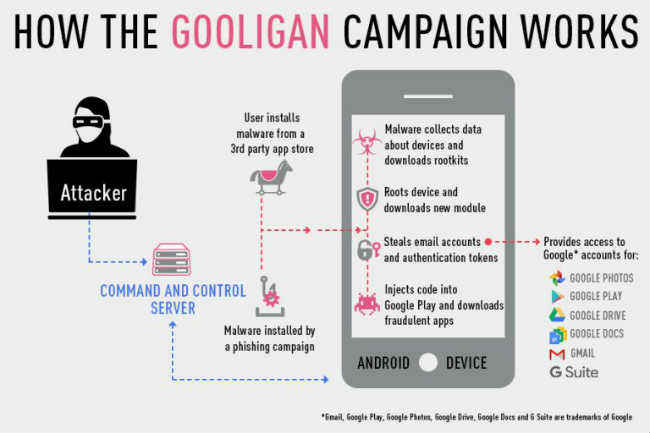
In a blog post, Check Point researchers wrote, "The infection begins when a user downloads and installs a Gooligan-infected app on a vulnerable Android device. Our research team has found infected apps on third-party app stores, but they could also be downloaded by Android users directly by tapping malicious links in phishing attack messages. After an infected app is installed, it sends data about the device to the campaign’s Command and Control (C&C) server."
The Check Point report notes that the rooted devices can download and install software capable of stealing authentication token allowing phones to access the owner's Google accounts and services. With Google token in tow, the hackers can access Google services like Gmail, Google Photos, Google Docs, Google Play, Drive and entire G suite.
The Check Point researchers further added, "After achieving root access, Gooligan downloads a new, malicious module from the C&C server and installs it on the infected device. This module injects code into running Google Play or GMS (Google Mobile Services) to mimic user behavior so Gooligan can avoid detection, a technique first seen with the mobile malware HummingBad. The module allows Gooligan to:
1. Steal a user’s Google email account and authentication token information
2. Install apps from Google Play and rate them to raise their reputation
3. Install adware to generate revenue."
Gooligan is an advanced version of 'GhostPush', a vast collection of Potentially Harmful Apps available outside of Google Play.
In response to this threat, Adrian Ludwig, Director of Android Security wrote in a blog post,"In the last few weeks, we've worked closely with Check Point, a cyber security company, to investigate and protect users from one of these variants. Nicknamed ‘Gooligan’, this variant used Google credentials on older versions of Android to generate fraudulent installs of other apps. This morning, Check Point detailed those findings on their blog."
Google says it has taken many actions to protect its users and has found no evidence of user data access or targeting. Google feels there is a need to strengthen android ecosystem security (which is going to be the case for any ecosystem) and is removing apps associated with Ghost Push family from Play Store.
If you are using third party app store on your Android device then you can visit Check Point's blog post for list of 86 affected apps. Alternatively, users can also check whether their Google accounts are breached by visiting this link. Affected devices can only be restored by reflashing with a clean Android ROM while affected Google accounts need immediate password change.