How to become a cyber-forensics expert

Get clued into the super-secret world of cyber forensics. Here’s how you can become a digital detective.
Cyber Forensics (or ‘Digital Forensics’) deals with evidence found on computers and digital storage media that’s related to crime scene investigations. If the idea of tracing back a crime to unravel the truth gets your adrenaline pumping, this is the job for you. While the skills required to collect digital evidence and data may be difficult to acquire, once you’ve mastered them, you can proudly call yourself the Sherlock Holmes of cyber crime. Though on the façade, digital forensics may appear different from real-world forensics, the sciences are quite similar at the conceptual level.
Information retrieval
Gathering evidence without contaminating the scene is a key part of the process. If you contaminate the source of evidence, the rest of the case is on an unsure track already. Which is why it is of foremost importance that evidence media − called “exhibit” in legal terminology − is examined with care. This means that the investigator must take a raw image of the media because doing so might reveal the tracks of the crime. If the original image doesn’t match this duplicate image at a later stage of analysis, forensics experts will know. The devil is in the details, so let us break down for you how information retrieval works:
• Data storage:
This part involves maintaining a file structure index and allocating actual data somewhere else. Technically, a B-Tree is maintained for storing the directory structure on each partition (letting users know which file and folder is inside which file/folder). The space for this B-Tree index is normally preallocated.
When you normally delete a file, it’s sent to your Trash/Recycle Bin which is just another folder maintained exclusively by your operating system. When you delete the file from your recycle bin, it remains on your computer because the only thing the operating system deletes is the entry from the folder structure (the B-Tree Index); the data remains in place. This leaves the window to retrieve deleted data open. This is the window that data-recovery tools use. Undoubtedly, data retrieval in crime scene investigation is of higher importance than mere recovery of photos, thus the demand for highly skilled recruits.
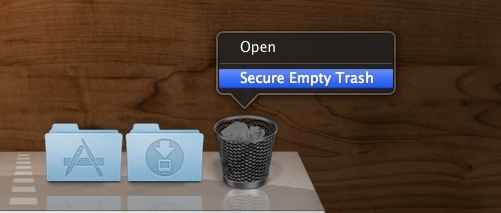
Mac OS X lets you remove the files in Trash securely without a third-party tool (just press Command key to show the option)
• Physical storage:
Data stored on a hard disk is stored as a sequence of bits, and each bit is physically stored by altering the magnetic value of a very tiny point on the disk. As imperfect as the world is, the magnetic value on the disk doesn’t reflect a perfect binary value. For example, if the original state of a bit was at perfect 0, firing an electromagnetic pulse corresponding to 1 will cause the value to come to 0.92. Now, if you fire an electromagnetic signal to set that value to 0, it would come to a state that would probably indicate a value of 0.1 and then again you fire the pulse to set the bit to 1. This time, it goes to 0.95.
Now, these values are fairly away from 0.5 and are easy to be determined as 1 or 0. However, if you notice the numbers above, a particular bit value can represent fair number of value overwrites on the same place. The accuracy of guessing the right value after x number of overwrites decreases as x increases. There are tools that do this fairly well. For one of these tools to work, they would need the exact magnetic value on the disk platter for each bit.
Not a lot of thought is required to conclude that to safely erase data from a disk. You’d need to overwrite the same disk portion where the data was stored, multiple times. The more random these values and more the number of overwrites, the lower the chance of correctly guessing the original value. The process of copying the bit-level detail of magnetic values on the disk is called “imaging”. This is done by taking a snapshot of the entire disk/partition and saving it as a file. There are tools available for this process and a typical imaging session takes a lot of time because of the excruciating level of detail required. Speaking technically, imaging must always be done on the evidence-disk (the disk on which the evidence of crime is suspected to be present) in the read-only mode.
Information/Data interpretation
Once the disk image has been taken, the next task is to understand what the data means. This step involves many tools and in-depth comprehension of the way
different pieces of software interact with each other to trace back the circumstances of the felony. You may also be required to understand the operation of the OS and/ or certain applications, which might have been used to commit the crime. While data interpretation is a complex process, we’ll lightly touch upon it to give you an idea of the work involved in this step:
1. Know the OS:
Data logged by operating systems sometimes plays a key role in determining what happened. Depending on the OS, the investigation areas might drastically change. Take Windows, for example; it stores a decent log of things that you try to do on the system. Activities such as installing an application and failed network login attempts are logged, and they can give a boost to an investigator’s perception of what happened. Sometimes, one has to look into the registry to ascertain the tools that were used or their settings (many tools on Windows store their settings in registry).
2. Fish for hidden file content:
The data stored on the disk makes up the largest part of the investigation. A number of times you may have to look at a stockpile of files that may appear useless to their original user, but will eventually prove quite useful. Autosave information saved by Microsoft Word or backup files generated when editing files by Linux OS are some of the mildest examples. The good as well as bad thing about these files is that they’re not visible to a user and normally just left on the disk by the OS or the program that creates them. In case they’re deleted, the normal deletion method is used. This would be the same as deleting a file from Trash or Recycle Bin, which means they can be eventually recovered.
3. Rely on tools to assist you:
At this point, you’re probably wondering how you’ll be able to read a Word document’s auto-save backup file. If you try to read the file in its raw form, your brain is bound to cheat you. That’s because it isn’t a plain text file. Registry is one of the creators of such a file. Interpreting the file will be impossible if you rely on our brains alone. You’ll need tools that can interpret the data you found on the disk. A simple example, here – MS Word can open a Word file recovered from a disk. Tools, formats and rights For dealing with data, you’ll need appropriate tools at each step. For example, if you want to extract the disk image from an evidence disk, there are many tools that can help you get the image. To create an image as well there are multiple tools available, from free and well known tools such as the ‘dd’ command on Linux to a complete set of forensic tools such as EnCase. Oftentimes, a single tool can’t be relied upon and one might need to, say, create an image using different tools.
File formats are crucial largely because they’re involved at almost every level of the investigation process. From extracting images to reading the data, one needs to deal with an extremely vast set of formats. Hypothetically, if you took the disk image using EnCase, then you would need EnCase to read the format in which the image file was stored. Assuming that your evidence disk was taken from an iMac machine, you’d need a way to read the HFS+ file system used by Mac OS X. Once the data is extracted, you’d again need software to read the data. If it’s a .dwg file, only AutoCAD would be able to open that file. You’d have to deal with a plethora of formats all the way. Lastly, you can’t simply start off with a forensic investigation and not have the required rights. you need to be a part of the police force or an investigative agency authorised to handle the case. And of course, you must have the right to use the software/tools involved.
Careers in Cyber Forensics
It’s by the virtue of the career opportunities that the attractiveness of a discipline is determined. Though not a popular field, Digital Forensics has opportunities in both the private and public sector. Interestingly, there are positions in both sectors where one needs to use this knowledge to destroy data, as well as recover it.
• Revenue Department:
Organisations dealing with money directly, both private and public need to trace financial crimes. This involves digging the data graves on the disk and creating the
timeline of who did what and in what order – challenging, interesting and intellectually rewarding.
• Malware Analysis:
Companies trying to create anti-viruses often need to inspect the patterns of data destruction as well trace malwares that may have deleted themselves after their mission was complete. Forensics experts are certainly a necessity here.
• Government and Police:
Crime investigations conducted by intelligence agencies, police and cyber security cells often require a forensics expert to help them walk a tightrope without falling off. With time, as electronic media takes over our lives, forensics is supposed to take over a large share of crime and thus, investigative processes.
• Private Auditing Companies:
There are companies that dedicate themselves to the job of Forensics Consultation needed by other entities. You guessed it right. These are private detectives.
• Trainer:
There certainly is a lack of talent in this field. Trainers are required at all of the prior mentioned organisations. And as it happens in many cases, being a trainer on rare and intellectually challenging cases is quite rewarding.
That being said, Cyber Forensics is an ever-changing landscape. New types of storage media and software are introduced all the time, ensuring new challenges to overcome keeping those in the field on their toes. You can rest assured that the environment will keep you updated on the latest in technology and in touch with a very wide array of technology.