How to bypass torrent blocks and safely download torrents in India

Torrents have been blocked, which is OK for illegal stuff, but what about legal torrent downloads?
Piracy hurts the people who create content, which is so good that you’re willing to pirate it just to watch it. That’s just crazy, right? Now we may feel strongly about piracy, but there’s something else we feel even more strongly about, and that’s censorship. While we’re all for stopping cyber crime, we’re never going to support the curbing of rights in order to do that. It is your right to use P2P networks such as torrent, and use it you shall, thanks to this article.
The government wants to block illegal content, and has instructed ISPs to do that, but we don’t think blocking off a technology as a whole is warranted at all. We refuse to be treated as guilty until proven innocent, and we want to be able to use P2P for legal file sharing. Honestly, we suspect the government isn’t interested in blocking the entire technology either, and we’re pretty sure you won’t be prosecuted for using P2P for legal file sharing.
How do torrents work?
In order to be able to know how torrents are blocked, you first need to know how they work.
When you try to download a file normally online, you usually click on a link or download button. This leads to your web browser asking the remote server (the computer on which the file is hosted) to send a copy of the file to your machine. This transfer is handed by File Transfer Protocol (FTP) or Hyper Text Transfer Protocol (HTTP). Now, the transfer speed, or more popularly, the download speed will be affected by quite a few factors – such as server load, protocol type and number of simultaneous ongoing downloads of the file. Almost all of this is different in the case of peer-to-peer file sharing.
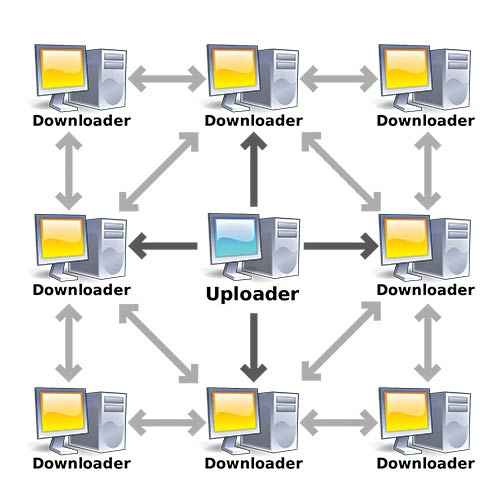
A basic diagram of how Torrent downloads work
First of all, there is a dedicated software client that takes your request and searches other computers just like yours for the file or a portion of the file that has been requested. These computers also have similar P2P software running in order to be able to understand the request. Once such computers are found, your computer starts downloading the file. BitTorrent or torrents in general take this one step further by offloading the tracking of other computers to a central server called a tracker. And torrents work on a tit-for-tat basis, meaning the more of the file you upload, the better downloading bandwidth you get. Also, the file is downloaded in multiple pieces from multiple machines to avoid bottlenecks and low speeds.
These pieces are then joined by the software to give you the file. However, your job is not done yet. If you keep uploading even after your file is completely downloaded, you get a good preference in the P2P system.
The Cheshire KAT
Much like the mysterious feline character in Alice in Wonderland, one of the biggest torrent networks in the world recently vanished into thin air. KAT (short for KickAss Torrents) operated under multiple domain names, all of which were seized by US authorities recently, along with the arrest of the person who was allegedly running the site. KAT was the Netflix of the torrent world, because it had a vibrant community that always reported fake uploads and rated audio and video quality accurately. It was also a good place to find esoteric stuff, which may not have been super popular, and thus hard to find.
It’s just a site, though, and uploaders have just moved on to other sites, which are now getting a lot of traffic that they just didn’t before. Sites such as demonoid, GloTorrents and 1337x are seeing an increase in the number of seeders and uploaders for all their torrents and all three of them come with a good reputation for content quality. You can also check out /r/torrents on Reddit to keep updated with the latest developments in the world of BitTorrent. Also check out this for a list of other torrent sites. May KAT rest in peace, we will miss it.
Unrestricted Access
It’s not just torrents that are banned from time-to-time. Sometimes sites such as PasteBin get blocked for silly reasons. While some believe it is the right of the ISP to block whatever it feels like (depending on whether you agreed to their terms), others are firm believers in the freedom of the internet, and specifically are against ISPs blocking anything, as their job is merely to provide a connection to the internet, and not to police it. Many others would say the same about the government, and not want anyone restricting what they do online, so long as it isn’t illegal. Thankfully, if you are against censorship, and your ISP or government is using technoolgy to censor things, you can use technology to unlock their locks. Here we will look at some of the ways in which you can do exactly that.
DNS Server
Very often, ISPs are lazy and block sites using their DNS servers. This means that when your PC requests the IP address of a site (say, pastebin.com) the ISP’s DNS server has been programmed to reply with a blocked web page. If you choose to use another DNS server, such as Google’s DNS servers (8.8.8.8 and 8.8.4.4), you might find that the site becomes accessible. This is because the ISP blocked pastebin.com at the DNS level, and didn’t block the IP address of the pastebin.com web server. Using a differnt DNS service is just the easiest way to get around this type of blocking.
Proxy
If changing the DNS didn’t work, you can choose to use proxies to try and access the content that’s blocked. Since proxies work for FTP and HTTP services, they’re perfect for browsers. You connect to a server that forwards all of your requests to whatever site you want to visit. While the request goes from the proxy server, they often pass along your IP address, so the site you’re going to knows who you are (or where you are from.) This is fine when your ISP is blocking something, but doesn’t work to bypass, say, geographical restrictions placed by the site you want to visit itself.
HideMyAss is an example of a popular web-based proxy. Proxies aren’t very reliable though, and only the paid ones are any good. Of course, the proxy itself might be blocked by your ISP, in which case you’re out of luck. PLus of course the slow bandwidth you get via proxies is made worse by all the ads that are displayed on their sites – hey, they have to make money some way, right? The biggest drawback of proxies is that you have to configure the proxy script or provide the details to each and every software of app that you have. Some software don’t even have this option, and thus, it can be a bit of a hit and miss affair.
SSH Tunnels
If you are looking for a way to securely access content over the TCP protocol, SSh tunnels work wonders. You connect to a server securely with an encrypted connection, and you can also use advanced port forwarding to, say, receive port 80 browser traffic at port 8080 instead. Of course you have to have a secure shell (SSH) account on a server somewhere, and then have the technical knowledge of how to port forward and use the SSH tunnel. This is easy to find with a Google search, provided you are comfortable with SSH clients and the command line. Any decent and reliable SSH service would be paid, however, and instead of paying for this, we’d encourage you to pay for a VPN instead.
VPN
A VPN, or Virtual Private Network, is a way of bypassing pretty much all forms of blocking and censoring. What a VPN does is route all of your traffic through their network, so that no one but you (your device) and the VPN provider (server you connect to) know which sites you’re visiting. As long as you can connect to the VPN service provider’s server, you can connect to pretty much anything online.
For example, let’s say you connected from your home in Mumbai to a VPN server in Nigeria. Now, any traffic originating from your machine will be first redirected to the server in Nigeria over an encrypted connection before it emerges online. Because most good VPNs offer encrypted connections, all that your ISP or government can see is the connection to the VPN server itself, but not the data that is being transferred, or the actual sites you are visiting. Remember though, that breaking the law can still get you prosecuted, and many VPNs have a detailed list of things you agree not to do when you join up, make sure to read that list.
There are quite a few good free options that come with both pros and cons. CyberGhost is one of the most highly recommended free VPN tools. It has a very easy to use interface and comes with a number of useful features like specifically restricting the amount of information you pass on to websites you visit, shutting down tracking cookies etc. The visual representation makes the actual workings of a VPN easier to understand. It does offer a limited set of options when it comes to servers, with the free versions mainly having European servers. Also, there is a three hour restriction on sessions.
Another alternative is Tunnelbear, with user friendly apps available for almost all platforms and one of the widest network of servers to choose from (only the India and Australia options are restricted in the free version). The catch here is the 500MB data restriction per month, which is pretty useless if you are using it to watch location-restricted videos online.
You also have a couple of options if you are looking to hide your phone, consoles and other connected devices as well. One such option is VPNBook, which doesn’t require any specific software and works once you enter specific information into your machine’s system settings. Keep in mind that this one is the most open of all the options suggested so far.
You can also access content that’s normally blocked in your geographical location thanks to a VPN. A VPN also helps when, say, you find that a lot of people are sharing a YouTube video on social networks that just doesn’t play for you. Using a VPN you could just choose a server in the US, or some place where the video isn’t blocked, and watch what all the fuss is about. Of course, the biggest disadvantage of VPNs is the fact that you’re adding a whole new route to all your internet traffic, and that is obviously going to add on a lot of response time to all of your traffic. This can be frustrating to some.
Tor
The Tor browser allows you to access the internet with total anonymity. It is very popular in countries such as Iran and China, where government censorship is pretty oppressive. It’s not at all recommended for regular browsing though, and certainly not for accessing sites you would normally enter passwords into, but for regular browsing, it can work when all else fails. The Tor network works by constantly changing the IPs you are connected to, which makes anyone trying to trace something back to you an almost impossible task.
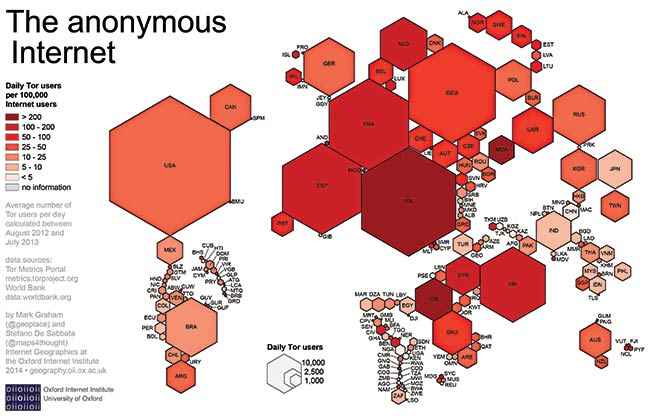
Infographic depicting global usage pattern of Tor
The developers of Tor have been up in arms against censorship of the internet, and keep updating their software that works even in cases where VPNs, proxies and SSH tunnels are known to fail.
Browsing on Tor can be super slow and painful though, because of all the randomising of IPs and all that.
Better be a jack of all
While it may seem that any one of these methods of getting access to your torrents and other P2P sites would work, it’s important that you learn all of them, because when it comes to digital security, privacy and freedom, each of these is a pretty good choice. Always remember, however, that each movie, game or song that you download without paying reduces the income of the artist – which may be fine for the multimillionaires who pretend to be pop-stars, but real musicians and artists can really suffer. While it’s important for us to inform you how to bypass silly restrictions on the internet, we still urge you to carefully consider staying on the right side of the law.
This article was first published in September 2016 issue of Digit magazine. To read Digit's articles first, subscribe here or download the Digit e-magazine app for Android and iOS. You could also buy Digit's previous issues here.