Rakshasa: The hardware backdoor that China could embed in every computer
It’s the Information Age apocalypse: What if, no matter how hard you tried, every computer on the market — from PCs to smartphones to fridges to cars — came pre-loaded with an irremovable backdoor that allowed the government or other nefarious agents to snoop on your data, behavior, and communications?
 Survey
SurveyBelieve it or not, we already have the technology to do this. It’s called a hardware backdoor, and it’s a lot like a software virus that grants backdoor access to your computer — but the code resides in the firmware of a computer chip. In short, firmware is software that is stored in non-volatile memory on a computer chip, and is used to initialize a piece of hardware’s functionality. In a PC, the BIOS is the most common example of firmware — but in the case of wireless routers, a whole Linux operating system is stored in firmware.
Hardware backdoors are lethal for three reasons: a) They can’t be removed by conventional means (antivirus, formatting); b) They can circumvent other types of security (passwords, encrypted filesystems); and c) They can be injected at manufacturing time.
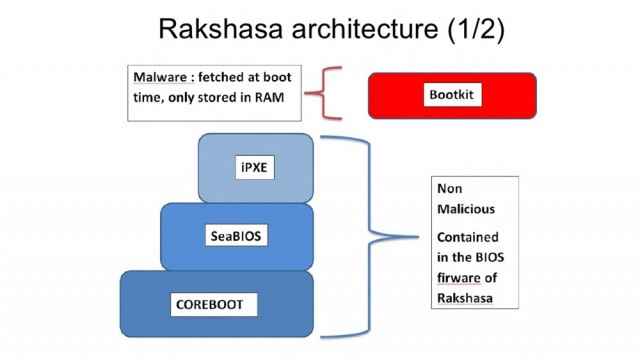
At the Black Hat security conference last week, assembly master and long-time security consultant Jonathan Brossard demonstrated a proof-of-concept hardware backdoor. Called Rakshasa (which are unrighteous spirits in Hindu and Buddhist mythoi), this backdoor is persistent, very hard to detect, portable, and because it’s built using open-source tools (Coreboot, SeaBIOS, and iPXE) it could be used by governments and still grant them plausible deniability.
To infect a computer with Rakshasa, Coreboot is used to re-flash the BIOS with a SeaBIOS and iPXE bootkit. This bootkit is benign, and because it’s crafted out of legitimate, open-source tools, it’s very hard for anti-malware software to flag it as malicious. At boot time, the bootkit fetches malware over the web using an untraceable wireless link if possible (via a hacker parked outside), or HTTPS over the local network. Rakshasa’s malware payload then proceeds to disable the NX (no-execute) bit, remove anti-SMM protections, and disable ASLR (address space layout randomization).
Because the same basic chips are used time and time again, Brossard says Rakshasa works on 230 Intel-based motherboards. It is also possible to load Rakshasa into the firmware of another piece of hardware — a network card, for example — and then have Rakshasa automatically transfer itself to the BIOS. Furthermore, the bootkit can be used to create a fake password prompt for Truecrypt and BitLocker, potentially rendering full-disk encryption useless. Finally, the Rakshasa bootkit even allows the remote flashing of the original BIOS — perfectly covering your tracks.
Rakshasa can be installed by anyone with physical access to your hardware — either at manufacturing time, or in the office with a USB stick. Fortunately, Brossard hasn’t released the code for Rakshasa — but he seems fairly confident that other security groups/agencies have already developed similar tools.
It is this last point that has been causing some political unrest in the US, and the rest of the Western world. As you undoubtedly know, China is very nearly the sole producer of all electronic goods. It would be very, very easy for the Chinese government to slip a hardware backdoor into the firmware of every iPad, smartphone, PC, and wireless router. Short of running every imported product through a very stringent series of tests and re-flashing firmware with known-good versions, this risk is unavoidable.
It’s also worth noting that many programmable (FPGA) and industrial chips already come with backdoors — sometimes by design (to ease development), and sometimes by mistake (the manufacturer forgets to remove the JTAG before moving to mass production). Again, this would give intelligence agencies a further layer of plausible deniability.
There is hope, though: BIOS’s replacement, UEFI, should be a lot more secure. UEFI offers low-level security through firmware signing — if the signatures don’t match up (i.e. they’ve been modified by Rakshasa), then the system doesn’t boot. UEFI Secure Boot has very little market penetration at the moment — but with Windows 8 requiring UEFI, that should quickly change.
This might only be a partial fix, though: I don’t know if UEFI will prevent other, non-BIOS/UEFI chips from being backdoored.
Copyright © 2010 Ziff Davis Publishing Holdings Inc