Petya ransomware: What you need to know
Not really, this new ransomware is actually more dangerous than WannaCry in some way, but also more amateurish.
The second major ransomware attack is breaking all over the globe, and with it a new form of terrorism is taking form. Governments around the world will have to deal with this eventually, but at the very least, these ransomware should raise awareness about cyber crime. The new ransomware bears some resemblance to WannaCry. That said, security researchers have said that it actually improves on that malware, employing new ways to spread and sidestepping the killswitch, that temporarily put WannaCry on hold.
But let’s begin with what this new ransomware is called.
Pety or NotPetya?
Security company Kaspersky calls this NotPetya, while others and most publications are calling it Petya. We did it too, right up there on the headline. Because…you know…trends and keywords (insert straight face emoji).
Nevertheless, the Petya name actually comes from an earlier malware by that name. Security experts found that the new ransomware bore some superficial resemblance to the original, it’s not actually the same. In fact, one security researcher says the NotPetya ransomware is designed to “spread fast and cause damage, with the plausibly deniable cover of ‘ransomware’”.
So, the name Petwrap, which has also been used by researchers and the media, is more accurate for this ransomware. It is also being called Bitdefender, Goldeneye, Petna and Pneytna. The point is, this isn’t Petya, it shares code with that malware and has similarities, but it’s a whole new cyber-monster on its own.
How does Petwrap spread?
As with WannaCry, Petwrap’s targets are primarily businesses. This means it spreads across a network really fast. It uses computers with administrative access to spread across the entire network. “A single infected system on the network possessing administrative credentials is capable of spreading this infection to all the other computers through WMI or PSEXEC,” says Kaspersky.
Further, the NSA’s EternalBlue exploit for Windows remains amongst the malware’s method’s of infection. This was used by WannaCry as well. But, Petwrap is more evolved, and uses other means to spread across computers. The following are the three methods of infection pointed out by Kaspersky Labs.
– A modified EternalBlue exploit, also used by WannaCry.
– The EternalRomance exploit – a remote code execution exploit targeting Windows XP to Windows 2008 systems over TCP port 445 (Note: patched with MS17-010).
– An attack against the update mechanism of a third-party Ukrainian software product called MeDoc.
The malware takes one of these three routes to spread across PCs. It starts with the Eternal Blue exploit, failing which it moves onto other attempts.
What does the ransomware do?
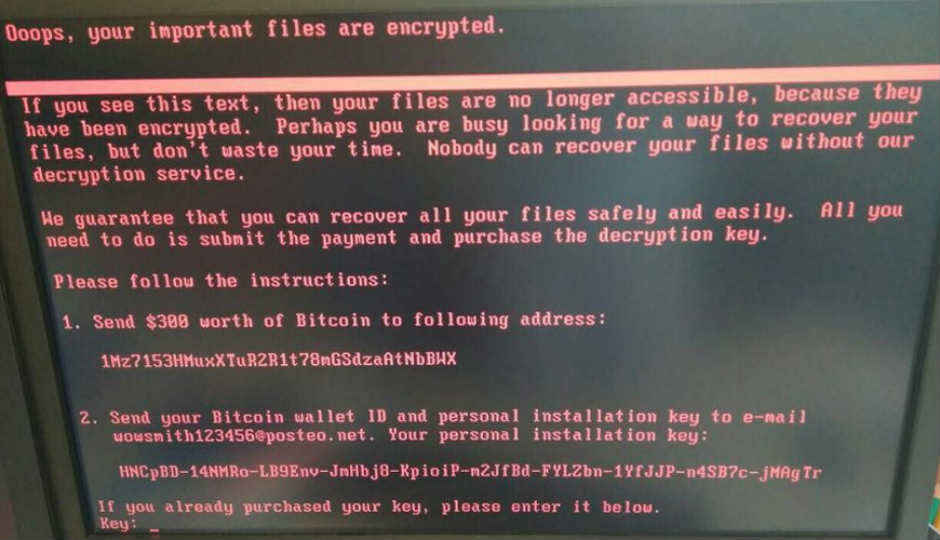
As with every ransomware, Petwrap also encrypts your files and holds them hostage for a price. Petwrap is asking users for $300 in Bitcoin to get back their files. Note that paying the ransom doesn’t actually guarantee access to the files, so you shouldn’t be paying the money.
That said, while most ransomware provide unique Bitcoin wallets and email addresses for each victim, Petwrap seems to use only one, hardcoded in the malware. This means suspension of that wallet would stop the attacker’s cash flow. In fact, the email address used has already been blocked by the email provider, meaning even if you do pay, you can’t contact the attacker.
This has also led researchers to believe that Petwrap is the work of amateurs and not serious cyber criminals.
How to avoid it
Kaspersky and Symantec have both updated their virus definitions to actively track the Petwrap ransomware. Of course, ensuring that Windows is up to date on your PC is the first line of defence, since Microsoft has already patched the EternalBlue vulnerability.
Further, it seems this malware looks for a read only file on your system. It’s called perfc.dat and it’s in the Windows folder in C drive. If it finds the file, then it doesn’t encrypt your files. So, that at least ensures that you still have access to your files. The malware will, however continue spreading from your system to the other, and it will encrypt files wherever the perfc.dat file isn’t available.
Who has it affected so far?
While the ransomware has reached Indian shores, it's biggest victims are in Europe and UK at the moment. Reports say many businesses in the Ukraine have been affected, along with companies from Russia and some other place. Indian subsidaries of foreign firms have also had to face the ransomware attack. For example, the country's largest port, Jawaharlal Nehru Port Trust (JNPT), has been hit by Petwrap as collateral damage. Petwrap hit shipping giant AP Moller Maersk, and spread to its systems wordwide, including those at JNPT.
It's unlikely that the ransomware will hit home users, but it still pays to be careful. The prevention mechanisms given above should be followed. Petwrap originated as a software update for an Ukrainian accounting software, called M.E. Doc, or at least that's what researchers from Kaspersky, Cisco and many others believe. That means we can't really warn you against downloading a specific email attachment or clicking on some link, but it also means the malware should be limited to businesses and computers connected to their networks.




