NotPetya is a wiper, not ransomware: Here’s what that means
NotPetya is meant for evil, it's not financially motivated.
The NotPetya malware breaking computers worldwide since Tuesday is not a ransomware at all. It’s a wiper.
 Survey
SurveyI’ve been watching the TV series Dexter recently, so let me explain this by drawing a parallel from that. Imagine two serial killers — one that has a code and only kills bad guys, while the other just goes about killing. The first killer has a purpose of sorts, he’s committing a crime, but in his mind he has a reason for it. That’s WannaCry, the ransomware that would take away access to your files, but it would do so to extort money from you.
On the other hand, Petwrap/NotPetya is simply destroying files on your PC, with no real intent to earn money. “The goal of this malware is pure evil. It’s not to make money, it’s to destroy data,” says Saket Modi, CEO of Lucideus, a cybersecurity services company. NotPetya is that second killer, who is simply a bad guy doing bad things.
Why did you call it a ransomware then?
That’s because the malware is cleverly made to look like one, possibly to get public interest going. WannaCry worked up quite a storm, and this new one wants to ride that into the history books. In reality, NotPetya could be a much more dangerous malware than WannaCry ever was.
You see, by definition, a ransomware encrypts your files, holding them hostage for a ransom. A decryption key is generated, that the attacker promises to give you when the ransom has been paid, usually in bitcoins. In the case of NotPetya, the files have not been encrypted in the first place, explains Modi. The malware is sort of deleting the data on your hard drive, and there was no decryption key to begin with.
“After an analysis of the encryption routine of the malware used in the Petya/ExPetr attacks, we have thought that the threat actor cannot decrypt victims’ disk, even if a payment was made,” wrote researchers from Kaspersky Labs, in a blog post. If there was ever a reason to not pay the ransom, this is it. Modi says there were very few payments made after the first few days, and researchers have seen no instances of decryption anywhere in the world.
So what is NotPetya then?
They’re calling it a wiper. “The goal of a wiper is to destroy and damage. The goal of a ransomware is to make money. Different intent. Different motive. Different narrative. A ransomware has the ability to restore its modification such as (restoring the MBR like in the 2016 Petya, or decrypting files if the victim pays) — a wiper would simply destroy and exclude possibilities of restoration,” writes Matt Suiche, hacker and founder of Comae Technologies, a UAE-based cybersecurity firm.
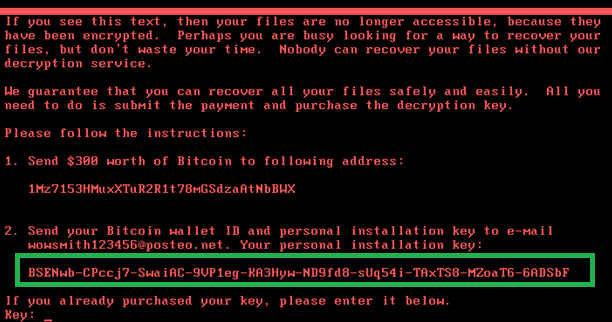
The image below is from Kaspersky Labs’ analysis of the malware. The highlighted portion represents an “installation ID”, which Kaspersky says is seen on most ransomware. This installation ID is unique for each victim, and attackers need it to produce the decryption key. On NotPetya, “the ID shown in the ransom screen is just plain random data”, Kaspersky writes.
This means that even if you pay the ransom, your data is likely lost forever. Secondly, it’s in line with suspicions that NotPetya was never financially motivated in the first place. Lucideus’ Modi also explained that while some data may be recoverable on SSDs and HDDs, flash storage-based systems will be completely wiped.
This is because flash storage doesn’t use layering of data and the classic RAM/ROM architecture (in SSDs and HDDs) isn’t used. So, when the malware writes to a disk on flash storage, it is essentially deleting all of its earlier data.
Am I safe?
As we explained in yesterday’s report, the means of infection for NotPetya remains the same. Updated Windows software will protect against the EternalBlue vulnerability, while there’s also a “vaccine” for this malware. You could simply create a perfc.dat file within the Windows folder, in read only mode, which stops the malware from deleting your files. It will still spread to other PCs on the network, but it will at least save your own data.