DNSChanger Trojan: History, Operation Ghost Click, Prevention and Cures

Today, on July 9, it is predicted that almost half a million people may lose internet access when the FBI will shutdown temporary DNS servers, impacting those infected by DNSChanger.
What Happened:
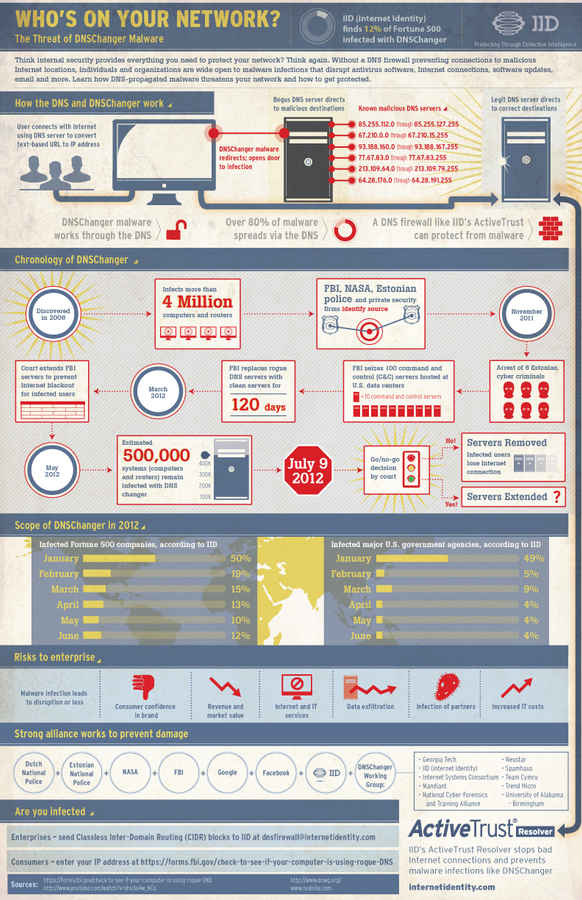
In November 2011, the FBI identified and located a ring of cyber criminals that had infected more than four million computers across the world with a Trojan known as DNSChanger.
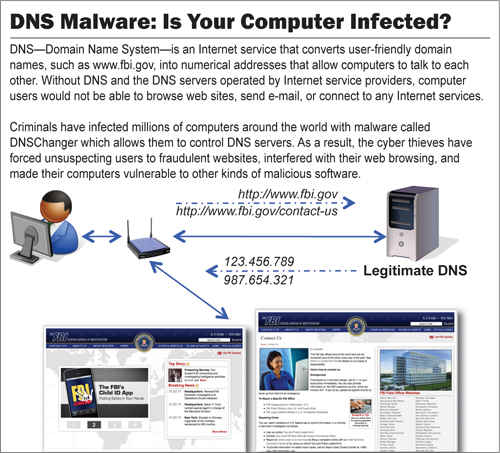
DNSChanger infiltrated both personal and corporate PCs redirecting computers to a set of DNS servers which directed Web searches to malicious Web sites.
Beginning in 2007, the cyber ring used a class of malware called DNSChanger to infect approximately 4 million computers in more than 100 countries. There were about 500,000 infections in the U.S., including computers belonging to individuals, businesses, and government agencies such as NASA. The thieves were able to manipulate Internet advertising to generate at least $14 million in illicit fees.
This is called “clickjacking” which is a technique where infected users think they are clicking on one website but are actually redirected to the fraudsters advertisement websites so they can get the click revenue stream.
In some cases, the malware had the additional effect of preventing users’ anti-virus software and operating systems from updating, thereby exposing infected machines to even more malicious software.
Not only were infected computers using rogue DNS services, but other home and work devices as well, including wifi-enabled mobile phones, tablets, smart HDTVs, digital video recorders, and game consoles. Basically, the criminals would change the web content that users downloaded to suit their needs and make money.
The FBI 2 year investigation called “Operation Ghost Click” broke up the conspiracy, made some arrests, and seized the bad DNS servers. But because a large number of PCs were already pointed at these servers, the Feds continued to operate them with clean and authentic DNS data.
The original kill date was going to be March 8 but the FBI was able to get a court order delayed it to Monday July 9th (date court order expires) so that people had more time to ensure their computers would not be impacted. According to DNSChanger Working Group, or DCWG, the number of infected systems has declined from over 4 million to just over 300,000 worldwide.
The impacted computers will not be able to access to the internet – this action will not remove the malware from those systems.
A report by IID (Internet Identity) indicates that machines at 12% of Fortune 500 companies and 4% of government agencies are still infected with the malware. When their systems are taken offline on the 9th it will lead to loss of productivity and may make it harder to service their customers.
Source: DNChanger Chronology Internet Identity
Source: FBI
RSA Commentary:
The internet shutdown will only impact a small % of the world’s actual internet user population. Many people took the delayed shut down from March to July seriously and made appropriate updates – impacted users are down from 4M to ~ 500K.
This unprecedented action by the FBI and will likely antagonize hacktivst who are concerned about the government having the ability to shut down portions of the internet.
People should ensure they will not be impacted by taking a couple of simple steps:
- Go to http://www.dns-ok.us. If the system is infected you’ll see a red image with the words “DNS Resolution = RED.” Alternatively, a green image with “DNS Resolution = GREEN” means that your computer is looking up IP addresses correctly.
- Ensure your anti-virus software is up to date
- Check your computer and router DNS settings to ensure it is not mapped to one on the FBI list
- If your computer is impacted you should:
- Backup your important files
- Reformat hard drive and reinstall the OS from scratch
- You could use one of the free tools below to remove DNSChanger
|
Name of the Tool |
URL
|
|
Hitman Pro (32bit and 64bit versions)
|
|
|
Kaspersky Labs TDSSKiller
|
|
|
McAfee Stinger
|
|
|
Microsoft Windows Defender Offline
|
|
|
Microsoft Safety Scanner
|
|
|
Norton Power Eraser
|
|
|
Trend Micro Housecall
|
|
|
MacScan
|
|
|
Avira
|