A look at online pentesting platforms

Being a techie youngling, you decided to learn some programming and as you kept mastering one language after another, you noticed that every tutorial starts with a hello_world.cpp, helloWorld.java and all the combinations of other extensions. But man oh man, where’s the h3ll0W0rld.leet to begin your journey in the pentesting and cyber-security world?!
 Survey
SurveyThe fire built within gets extinguished real quick when no proper beginner-friendly entry points are present in a field you are interested in. According to ISC2, the unfulfilled job positions in the security sector are soaring with a number of 2.8million jobs without suitable applicants in 2018, projected to hit even higher numbers by 2021 . To combat these woeful numbers, we will introduce you to great platforms to push the progress forward in your journey towards becoming a hacker.
A lot of platforms are available on the Internet, we chose only the ones that are the most helpful from a practical viewpoint and are respected in the security community. Mainly, platforms provide facilities to hone your security skills in two major ways: challenges and labs/machines. Challenges are isolated problems focussed on specific topics, for example, to teach buffer overflow techniques, binary file alongside its source code might be provided. These can be looked at as the questions posed in a CTF. On the other hand, platforms providing labs/machine put you in a real-life like environment that mimics the conditions that might be faced by an actual security professional. These labs may be remote or available on a local system. We’ll be using machines/labs/boxes interchangeably, so don’t get confused as they all mean the same thing.
Platforms providing labs
Now let’s take a look at some of the platforms which will force you to think like a professional and let you get a taste of how things work in the wild.
1. HackTheBox
[https://www.hackthebox.eu/]
This had to be the first in our list because well, of course, they provide some of the best resources and are highly respected in the security community. HTB really puts your skills to test, even the sign-up procedure requires a bit of hacking! You need an invite code, but unlike every other invite-system, here the invite code is given by the website itself and not by another user, albeit a little reading between the lines is required.
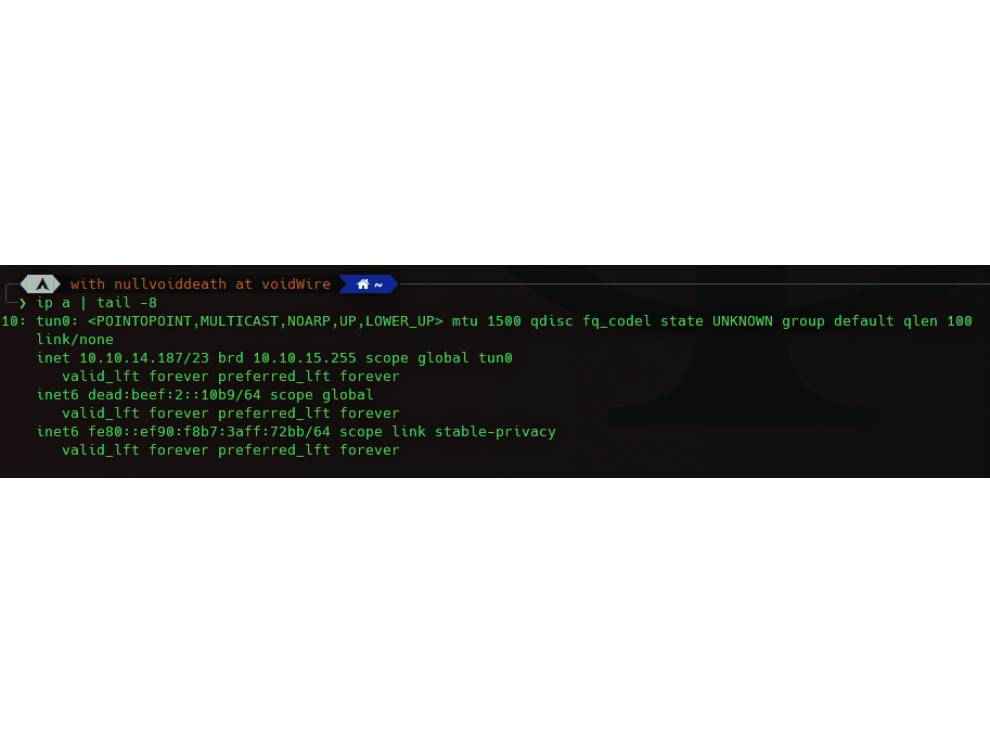
When you succeed in logging in, you will see yourself presented with a dashboard. All the machines are located on a virtual network managed by the platform. So, as to connect their network and access the machines, the dashboard which will provide you the “.ovpn” file, which is used with the OpenVPN tool. This will link your computer through a virtual link to their network. You can check whether you are connected or not by running “ip a” command from a Linux terminal. If you see a “tun0” entry, that means you are in. The IP starting with “10.10.x.x” will be used by the other machines on the network. This will be extremely useful when doing basic exploitation, file transfer, etc.
After you have done your IP configurations, the rest is simple: select a machine(called a box), submit the user and root flag hidden in a box and you will “0wn” it. But here’s the catch, root flags can be read by users having, as the name suggests, root privileges and user flags can be read by the specific “fictional” users of the box. And to even get to these flags, let alone reading them, you need to exploit, leverage and pivot all the way. At a specific moment, more than one member can be working on a single box. Even though there are a lot of servers available, due to the huge popularity of HTB each server is buzzing with budding hackers, so it’s not unseen that someone mistakenly (or deliberately, in case of a jerk hacker!) alter the machine causing hiccups in others' progress. To tackle this, a reset button is provided for each machine that’ll set the machine to its default state. These boxes are created by community members and curated by the HackTheBox staff. Boxes’ difficulties include levels Easy, Medium, Hard and Insane but these ratings are often misleading where medium boxes are harder than hard ones and insane boxes are easier than the medium ones. Word of warning, the machines may not be *cough* noob-friendly *cough* but the HTB community focuses more on learning. The HTB forum[https://forum.hackthebox.eu/] and their discord server[https://discord.gg/hackthebox] is a great place to start whenever you feel you have hit a roadblock in your pentesting experience. A rank system is also present which consists of the following promotion levels:
Noob->Script Kiddie->Hacker->Pro Hacker->Elite Hacker->Guru->Omniscient
The ranks are determined by the overall percent completion, inclusive of both labs and challenges. No demotion system is there, hence once you achieve a rank, you’ll have that regardless of your activity status. But as soon as a machine retires, the points are deducted and the overall completion decreases. A new machine is introduced and an old one is retired each week, so you need to keep up your pace if you want to rank up! The maximum rank we have achieved is Elite Hacker (yes, we are flexing).
Alongside the labs we discussed above, several challenges are also provided making HackTheBox, a hybrid of labs and challenges based platform, a leader. Numerous categories are present like steganography, cryptography, binary exploitation, etc, each having a number of challenges. Again, these challenges are created by the members and approved by the staff. After a period of time, each box and challenge is “retired”, that is, it is taken off the active listing and only after retirement the write-ups and solutions are allowed to be posted online. A paid VIP mode is available, in which retired boxes and challenges are available to exploit, but the free mode is more than sufficient to get the expertise.
Recently, HackTheBox released an official (ISC)2 CPE Submitter, meaning users can earn CPE credits as they progress through machines and challenges which are considered an industry standard about the experience one has in a specific field. Alas, this feature is only available to VIP users. Here are some platform specific guidelines regarding good conduct that you should follow to keep the community and the platform enjoyable for everyone:
Since you are not alone while working on a box, it’s suitable to first properly research your methodology so as to not to brick the online machine environment.
Always remove your traces and any material you might have used to further your progress so as to not spoil the tasks for others. This includes custom scripts, uncovered passwords, retrieved flags, etc.
Don’t remove the user and root flags from their predetermined directories.
Below are some resources which are specific to HackTheBox. They are mostly walkthroughs and write-ups of past boxes and we can’t stress enough how crucial are these to get the correct mindset and the approach required to successfully smash through the boxes:
“IppSec” channel on YouTube [https://dgit.in/IppSec]
Ahmed Hesham’s blog [https://dgit.in/AHblog]
2. VulnHub
[https://www.vulnhub.com/]
True to their motto “Vulnerable by Design”, VulnHub is a platform that provides user-created machines with loopholes and exploitable vulnerabilities deliberately present in them. VulnHub is different from HackTheBox since each vulnerable machine needs to be downloaded and imported to a virtualization software. If you are unfamiliar with the term “virtualization”, it means that different operating systems and applications can be installed on top of your current system, without getting your hands dirty with your physical system. So, if you have all the required tools, you don’t need an internet connection to practice your hacking skills! No hassle of config file downloads and no VPN setups.
As virtualization is involved, you need to make sure it’s enabled in your system. Usually, virtualization is enabled by default and if not, you can always tinker with your BIOS settings to do that. You must have heard of VirtualBox and VMware (Player or Workstation), them being the big guns when it comes to virtualization at personal and consumer level. While VirtualBox is an open-source initiative by Oracle, VMware provides paid software but their VMWare Player is available for free if used for non-commercial purposes. Most of the machines are compatible with both of these software, but some are crafted with a specific software in mind. If you are comfortable with either VirtualBox or VMWare, a number of methods are available to import/convert machines from one format to another. Most popular formats that machines are available in are as follows:
Open Virtualization Format (.ova, .ovf): The machine is supplied as a whole package and as a result, file sizes can reach up to 4 gigs. These are supported by both VirtualBox and VMware software. No extra configurations are needed, just import, launch and get hackin’-crackin’.
Virtual Machine Disk(.vmdk): The virtual hard drives that are attached to the virtual machines. The extension was developed by VMWare and VMware Player supports it natively. Usually a ‘.vbox’ file is supplied with all the configuration already specified and all you have to do is run this with the software, but this is for VirtualBox. But as we said, any appliance can be exported as a “.ova” file from within the software and used with other virtualization software.
Unlike HackTheBox, there are no individual challenges belonging to particular categories that are present on VulnHub, making it a purely lab-focussed platform. Again, machines are available and approachable with users of any experience and machine difficulty is usually mentioned in the description. VulnHub is community-driven as all the vulnerable virtual machines are created by fellow users and approved by the moderating staff. Even though no officially maintained forum is present, VulnHub recently got their own discord server[https://discord.gg/uHn4xdb] where updates about new machines, write-ups, etc. are constantly posted. That’s the first place we’ll start looking for some help in case of getting stuck.
VulnHub provides a clutter free web interface to download machines to your liking. No sign-up or login is required, each machine comes with their defined goals( either to uncover a certain amount of flags or gain root privileges). Here are some of our recommendations and general guidelines:
VulnHub will be a better place to practice if you are on an unstable internet connection. You don’t want to face delays due to other users doing the same machine you are doing. But then again, you can play around on both HTB and VulnHub.
Keep your pentesting environment( the OS you’ll be using to hack the machines) and the vulnerable machine on the same virtualizing software and same network settings (NAT, Bridged or Host-only).
The best option is to keep both the systems as NAT, that has worked well for us in most cases.
We recommend to use VMWare Player as it provides a more fluidic interface and easier configuration. Still, at the end of the day it’s about what you feel comfortable working on.
A lot of other online lab platforms are available like PentesterLabs, VirtualHackingLabs, etc, but the most useful resources are either paid or are connected to some certifications they sponsor, hence, we chose the above two platforms which are best for beginners. Now let’s take a look at the challenge based platforms.
Platforms providing challenges:
Instead of simulating real-world applications, these platforms provide challenges to hone your skills in various sub-sectors of cybersecurity interests be it web application hacking, cryptography, reverse engineering and or anything really! Challenges from different categories act as the building blocks for all numerous labs and practicing challenges is a great way to hone your skills.
1. HackThisSite!
[https://www.hackthissite.org/]
This has to be one of the oldest stomping grounds for hackers across the world. Created by Jeremy Hammond (hacker known by the handle “xec96”, popular for whistleblowing and hacktivism) in 2003 as a “hacker training ground”, it is a pretty respected website for acquiring the skills and mindset of a hacker.
Challenges are divided into 10 categories like Basic, Realistic, Forensics to name a few. We highly recommended beginners to start with the basic missions which will motivate you and prepare you to take on harder problems.
Basic challenges are mostly isolated and focussed on a specific set of skills. On the other hand, Realistic challenges may require knowledge from one or more domains. Some interesting categories like Phone-phreaking challenges, IRC (Internet Relay Chat) challenges are also present which are rarely seen on other platforms. Most of the challenges are created by the HTS staff and moderators while some are crafted by the members. Like the HackTheBox, a ranking system is used where you can attain the ranks in the following order,
Pentitioner->Script Kiddie->Apprentice->Wiseman->Master->Hacker->Elite->Sage
Ranks are determined by the number of points you have which you earn by completing the challenges. A special ‘Hacker Emblem’ is also there but it’s only given to “those who deserve”, according to the website.
A highly efficient forum is maintained where the challenges are discussed extensively. As the platform is quite old, you might not get your questions answered quickly but then again there's a 99% chance that what you are looking for has already been asked and solved, so make sure to check the forum thoroughly before posting. Other than posts about challenges, the forum is brimming with information ranging from hardware to gaming, book discussions to telecommunication. Being one of the older platforms, they haven’t migrated to newer platforms like Discord or Slack but they are still active on their IRC channels, so remember to check out that if you feel the need. HackThisSite is strongly recommended if you are an absolute beginner as it’s the right place to get the taste of the hacker culture.
2. Root-me
[https://www.root-me.org]
Like HackTheBox, Root-me is another hybrid platform providing both challenges and labs, but while HackTheBox is a lab-focussed platform providing challenges, Root-me is a challenge-focussed platform providing labs. The number of challenges present on Root-me is more than any other platform we have ever seen and you’ll never run out of material to practice. Some categories have more challenges than others, but each has enough(for example, App-System category has a 73 challenges!).
There are a total of 11 categories, with the standard cybersecurity topics like steganography, cryptoanalysis, etc. An interesting “Network” category also exists which deals specifically with analysis of captured network traffic including different protocols. Solving challenges here will be a great way to strengthen your grip on protocols which plays an essential part when you actually encounter the network entrails while reviewing a web application or pentesting an online system. Challenge creators include admins and users, but mostly admins. A ranking system is also present, where you can rank-up from newbie to a lamer, on to programmer, hacker then finally elite.
Labs on Root-me are in a section called “CTF”, where there 40 rooms available. You can choose any empty room, select a vulnerable environment and complete the requirements. Any player can join the room, and the competition (of sorts) ends when someone enters the final flag or when the timer run-outs, whichever is first. We noticed that most of environments were virtual machines from VulnHub, so this is basically like an online version of selected VulnHub machines.
As far as the community goes, a forum is present. As mentioned above, Root-me, being a challenges focussed platform, cover the major portion of the forum with a separate topic for each category where problems belonging to that categories are discussed. Just like HackThisSite, Root-me has its own IRC channel and they are pretty active there. There’s a chatbox present in the sidebar of the website which can be used to communicate with other members.
Honorable Mentions:
Here some platforms didn't not quite made our list but are still pretty helpful. So, you can check them out if you want some more options.
1. The Web Security Academy
[https://portswigger.net/web-security]
“The Web Application Hacker’s Handbook(WAHH) ” is considered a holy-grail when it comes to web application pentesting. In the olden days, the website used to have solutions to the problems present in the book and related labs, for which you needed to on hourly basis. But recently Dafydd Stuttard( known as “portswigger” and the creator of BurpSuite) who authored the book, presented Web Security Academy as the successor to WAHH where all labs are free of cost, covering all the topics of web security. Solutions are also present, in case you get stuck. Make sure to check it out.
2. OverTheWire: Wargames
[https://overthewire.org/wargames/]
The aim of this website is to teach Linux and security concepts through games which will keep you engaged and they are quite fun as well. Different levels are present and a recommended order to go through the levels is present on their website. The easiest and most popular level, Bandit, teaches Linux and networking concepts in a pretty interesting manner. Each level can be accessed through a Secure Shell (SSH) connection and URLs are present in descriptions. To proceed to the next level, you will need to solve the previous since it will contain the password needed for the next level.
3. HACK.ME
[https://hack.me/]
A sandbox which provides mainly vulnerable web applications, which you can access on the fly without any configurations. The activeness of the community seemed pretty low to us as the last revision done a sandbox was on 10th April 2019. Still, there's no harm in exploring and having fun with the machines because you never know what you might learn.
additional guidelines:
Even though security is hard to get into, it’s not impossible. Security community, be it on Twitter or Discord or Slack or anywhere, is one most supportive ones we have seen. Here is some technical and social advice we wish someone had given us when we first started out:
Get into habit of making notes. Each step you do, each hack you perform, each exploit you create, make sure it’s well documented.
Before approaching someone with your questions, do your homework and research. While most of the people will surely help you, some are busy or get too many such questions that they might lash out on you which might demoralise you, so make sure to try as much as you can on your own.
While choosing a pentesting toolset you can either choose Kali Linux [https://www.kali.org/downloads/] or ParrotOS [https://parrotlinux.org/]. You can also select a distro of your own liking and add the required tools. Windows is not at all recommended.
Don’t share spoilers. If you are helping someone, guide them to the right approach instead of just giving them the answers. Learning is most effective when done on your own.
Conclusion:
Spending enough time on any of the platforms mentioned above and grinding with persistence is sure to enhance your skills to a point that you can start considering cybersecurity as a career option rather than just an interesting hobby. It’s time to step up your security game. Happy Hacking!