You’ve Been Warned Big Business. Ransomware is Coming for You!

Ransomware is growing and adapting faster than you think. Big businesses, you are not as secure as you think. The delta between perception and reality will be a costly lesson for organizations, impactful for customers, and a financial windfall for criminals.
My message to CISOs, CSOs, CEOs and board members:
It will get far worse and Ransomware is just one aspect. Act now in a strategic way where security becomes effective and affordable in a sustainable way. Proper cybersecurity is now the cost of doing business in the digital world.
The latest variants such as WannaCry and more recently Petya are just stepping stones on a long journey ahead. Ransomware was originally focused largely on consumers, but took the jump and expanded to businesses well over a year ago. It will never step back. The reason is simple: money. Businesses are heavily reliant on data, connectivity, and digital assets. They also have the financial resources to pay very large ransoms. Recently a company paid $1 million to ransomware cyber criminals.
Consumers were originally targeted as they were easier to victimize. Ransomware code was rudimentary and sufficient to dumbfound most non-savvy consumers. Ransom demands started in the low hundreds of dollars, usually paid via gift cards or Bitcoin cryptocurrency.
Businesses were a tier higher and most employed basic anti-malware and network filters sufficient to be a barrier to immature attack code.
In the past year, the economics and scale have changed. As ransomware code became more professional and authors more responsive to incorporate new vulnerabilities, businesses were well within reach of these tools. Ransomware adapted beyond just encrypting documents and photos. Entire databases, web pages, backup files, and intellectual property could be held for ransom. The financial demands began climbing for consumers, with the price to recover files exceeding over a thousand dollars in some instances. But the revelation for professional crews was that businesses have deep pockets and they would pay if the right data was held.
Logic tells the story. Why infect grandma and hold her family pictures hostage for a few hundred dollars, when you can target a company and score tens of thousands or even a million dollars?
Criminals are extremely predictable in one way, they are greedy. Applying the Greed Principle, which basically states that – if a thief can steal $10 from you today, they will attempt to steal $15 from you tomorrow. Businesses are now squarely in the danger zone and savvy criminals will pursue these targets with relentless ferocity, even competing with each other to score the best targets. Not that they have to compete anytime soon. It is a target rich environment right now. They even have the luxury in helping each other by sharing code, victim lists, best-known-methods, providing mentorship, and selling vulnerabilities.
Businesses simply have no idea what they are up against and ransomware is just part of the problem.
Crying Wolf
Security professionals have been ringing this warning bell for close to three years. Some actions have been taken, but largely it is an apathetic race to find the minimum acceptable commitment that satisfies regulations and executives, without consideration of how the threat will maneuver and evolve.
Ironically, the security industry is also to blame. Many times, it is the security vendors who fuel the flames of fear to drive sales. Often I see small companies trying to break into a market or sell a niche product, use this tactic. I think the worst offenders are the research-for-hire companies that will always generate reports to the benefits of those who they are contracted with, that are creative with statistics and surveys to propagate obscure risks or overestimate impacts.
Promoting Fear, Uncertainty, and Doubt
Fear only sells to the fearful. The well informed don’t need to be sold, rather they are actively pursuing the best capabilities to manage the complex risks they face. I am no salesman, just a strategist who knows the opposing forces and the battleground. When I say ransomware is a serious risk, I have no secret agenda. I believe we must collaborate to share information and insights. As a community, we are stronger when we all work together. My blogs and topics are neither a threat nor an attempt at fear mongering. It is a reaffirmation that common sense and good advice are out there, to help organizations optimize their security posture and achieve the right balance of spending, risk management, and usability. We are all on the same side, trying to protect the digital world that encompasses security, privacy, and now intersecting with our physical safety.
Two Camps of Failure
Many if not most, businesses have invested some resources and attention to cybersecurity. Many times it is to satiate regulations or put up a façade of basic controls to be considered on par with their peers. The real test is not what you spend, but how effective it will be against future attacks.
Far too often we prepare for past battles. The Maginot Line bankrupted France after WWI. It was a defensive monolith that protected the eastern front of France from aggressors. Formidable against tactics seen in the Great War, it became laughable as WWII started and Axis powers easily bypassed it to take Paris. It is not about how defenses fare against old tactics that matter. France was vulnerable behind the greatest fortifications ever built but didn’t know it until it was too late.
Cyber threats are rapidly evolving in tactics and capabilities. They are at the forefront of using new technology to their advantage in almost all cases. The modern equivalent of vulnerable businesses falls into two basic camps.
First, there are those hiding – They have largely ignored the warnings and have not taken cyber risks seriously. They know their defenses are not strong, hope every day that they are not attacked. Although they may have basic defenses, they would not repel a directed attack against any type of persistent threat. Hope is their strategy. These are the executives who worry at night that their systems, products, and services might be brought to their knees at any moment. They too are the ones who quietly plan their exit strategy if the situation quickly goes south, as many executives have been losing their jobs after successful attacks.
The second group is in a better place, but overconfidence and complacency will be their undoing. Over the years they have invested in technology and staff to put a number of controls in place. They have a few crown jewels they rely upon, and seem confident. They have basic metrics and pretty charts to show boards, partners, and staff. They feel good. So much so, they may even be looking to scale back.
These are the ones who will be truly surprised when they are compromised. Their defenses seemed strong in the past, which led them to coast and be lackadaisical. Vigilance against intelligent opponents is not about remaining static, but rather maintaining an understanding of what the enemy can and will do in the future.
The end result for both of these camps is the same. They will be compromised in a significant way and have difficulty coping with the aftermath. It is just a matter of time.
What Enterprises Need
Businesses must apply best-known practices, which are constantly evolving to maintain a strong cyber defense capability. Here are the 5 recommendations I have for large organizations (small ones too if they deem relevant).
1. Look Ahead. In most complex direct attacks, the organization did not see the attack coming because they weren’t looking. Sun Tsu professed to know your Enemy, Yourself, and the Battlefield. Great lessons. Gain forward insights to those who are likely to attack you, their preferred methods, and how early indicators of an attack will appear. Be in tune with your critical assets, networks, users, and data.
You have home-field advantage, so use it. Lastly, know your systems and their vulnerabilities. Those armed with the knowledge of what is coming and how it will affect them will have an advantage.
2. Leverage Technology. Strong technical security solutions enable vital elements of system protection at speed and scale. Leverage the best technology for your organization and market. At the very minimum tools to protect network connections, email and web gateways, data at rest, authentication, client end-points, and server/cloud environments is needed as a foundation. Depending upon your business and the class of attackers you face, it is likely you will need to supplement with other solutions as well.
3. Behavioral Controls. For anyone who has heard me speak at a security conference, I always make a point of talking about what is invariably the weakest point in any system: the people. I would rather have a well-informed, motivated and security savvy workforce instead of a stack of firewalls. Persistent and reinforced behavioral controls are crucial to not only prevent compromises but also detect and respond to them. People are the greatest variable – they can be the biggest weakness or the most important security asset. Start with clear policies, training, and support originating from the C-suite to make effective changes. If employees can’t describe the security expectations of their CEO, then you have a problem.
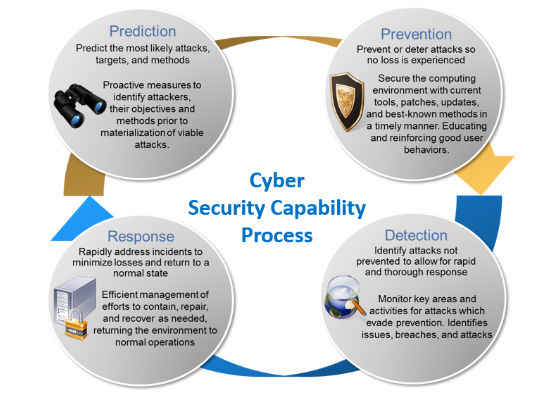
4. Processes are Required. Solid business processes for strategic planning and operational capabilities is the glue that pulls and binds everything together. The overall design and operation of a top-tier security organization revolve around an interlinked and repeating process of Prediction, Prevention, Detection, and Response to threats.
5. Executive Teamwork. Security is a team sport and cannot be achieved alone, even with a star player. Collaboration across the executive table (CIO, CTO, CEO, CFO, Legal, CHRO, etc.) gains in importance every day. All management branches are key to business, therefore, are valuable. As such, keeping the confidentiality, availability, and integrity of that value is also important to the organization and stockholders.
This roundtable must achieve 3 goals. First, be savvy with regards to the threats their group faces, the likelihood of being attacked, and the impacts of thse incursions. Second, understand they must play an active role in defining acceptable risk and then being responsible for it. Third, through collaboration they must realize they can positively improve the defensive position and trust of the entire company.
Chief Human Resources Officer (CHRO) for example must protect the confidentiality of their records, but can also play a pivotal role in vetting new hires, training security standards, promoting good practices, and enforcing a security policy to all employees and contractors.
This has an amplified effect across the entire organization. Each C-level office has similarly unique opportunities to contribute to a more secure business.
Maneuvering strategically to permanently incorporate security into the fabric of a business is required in the future digital age. It takes planning, technology, good behaviors, process, and teamwork. Failure will be painful and likely public, facing greater scrutiny as expectations from regulators, customers, and partners continue to rise.
Take Action
Apathy is the killer of success. Regardless of your confidence, you are already behind, and attackers are outpacing defenses even as we speak. Advances in technology continue to be exploited by attackers before defenders. Time is on their side.
For those responsible for the success of their organization, division, or group, action must be taken. Complacency, hope, and ignorance are no longer viable paths. Find the courage to identify the best path forward to actively manage your cyber risks and achieve the optimal balance of security moving forward.
For more such intel IoT resources and tools from Intel, please visit the Intel® Developer Zone
Source:https://software.intel.com/en-us/blogs/2017/07/17/big-business-ransomware