This Ransomware Turns Victims Against Their Associates

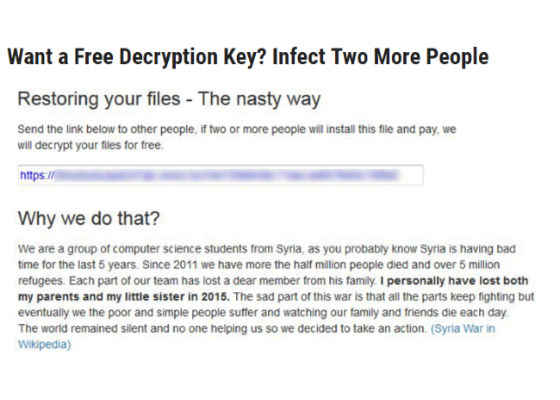
Popcorn Time ransomware, a newcomer to the malware scene, has an incentive program for victims. If they successfully infect others who pay, they will get their files unlocked for free.
Sacrificing others to save your own files. This is a new scheme by ransomware authors to increase infections and maximize extortion returns.
Friends and Enemies
Popcorn Time is creative and interesting from a social-experiment perspective. Who would intentionally infect others to unlock their own files?
Desperation, curiosity, pack-mentality, primacy perceptions, and those who have an internal evil spark to redirect harm to others they dislike, may take up the challenge to pass along this ransomware. Whatever the reason, the likely victims will probably not be on the lookout and we be easier to infect.
The most interesting aspect will be what happens next. Will the evil collaborator then work to convince the infected party to pay the ransom? They only get a free key if they contaminate two people who pay the extortion. How far will they go? Such social games would be a worthy study of any psychology class.
Trust is the Currency of Security
Popcorn Time is one of many ransomware engines that are floating about looking for victims, but its behavioral and infection approach sets it apart. It is attempting to use the trust of its victims to spread.
If you can’t trust your computer it is a technology problem. If you can’t trust your friend, neighbor, colleague, yourself, or coworker it is a behavioral problem. As Popcorn Time proves, the realm of cybersecurity includes both.
Malware writers, especially the ransomware community, are pushing the boundaries of creativity to achieve their goals of monetary gain. Expect them to explore more ways of subverting and manipulating trust to support their purposes.
The Code
The code appears to have a number of new and latent features, yet to be activated. At least 2 variants are already out in the wild, with more advanced versions likely to emerge as the author(s) refine their engine. Removal of the code does not appear to be too difficult, but the encryption of the compromised files remain even after the malware is removed. Decrypting the files typically requires the master key, which is in the hands of the extortioner. I have not seen a 3rd party decryptor on NoMoreRansom.org as yet. The best option for victims is to restore files from backups. Paying a ransom is not recommended as it puts money in the hands of criminals which reinforces the continued growth of this epidemic.
Et tu Brute? – Julius Caesar
I don’t expect Popcorn Time to get many takers of their offer, but it does open a few doors to negotiate for different advancement paths for the attackers. Passing infections is not unheard of in history and this may appeal to a few, so be wary just the same. That guy in the corner office, who never liked you, might be sending you an unpleasant web link which would explain his evil grin.
Popcorn Time is breaking new ground and I am interested to see how this evolves on the behavioral side. Always something new in cybersecurity.
For more such intel Modern Code and tools from Intel, please visit the Intel® Modern Code
Source:https://software.intel.com/en-us/blogs/2016/12/14/this-ransomware-turns-victims-against-their-associates