Overview of an Intel Software Guard Extensions Enclave Life Cycle
Life Cycle of an SGX Enclave
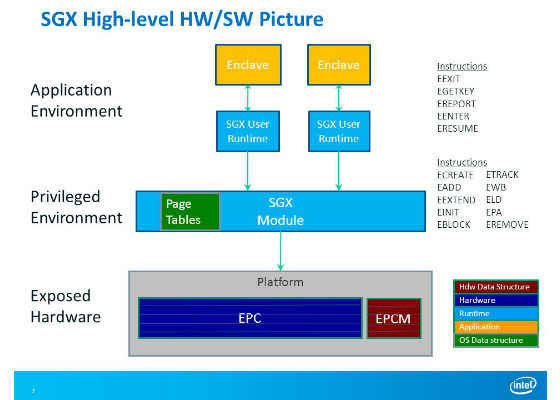
SGX Enclave:
- Intel SGX provides hardware features that creates a form of user level TEE. The enclave is an isolated region of code and data within applications address space.
- Data within an enclave can be accessed by only with code within the same enclave.
- The enclave is able to protect its data using Enclave Page Cache (EPC); a secure storage used by the processor to store pages when they are part of an executing enclave.
- The EPC is built from chunks of 4KB pages; aligned on a 4KB boundary and each page has security attributes in the Enclave Page Cache Map (EPCM), an internal micro-architecture structure that is not accessible by the software. It tracks the content of each EPC page, and enforces access control for accessing the pages.
- A Cryptographic hash of the code and data residing in an enclave at the time of initialization. The measurement is used to verify that the loaded enclave is what the enclave claims it is.
- An enclave is a protected area in the application’s address space, which provides confidentiality and integrity even in the presence of privileged malware.
- Attempted accesses to the enclave memory area from software not resident in the enclave are prevented even from privileged software such as virtual machine monitors, BIOS, or operating systems.
- It provides a safe place for code and data in application. Intel provides some special hardware instruction to create and support enclave. Intel SGX enclave memory is protected even from privileged software.
SGX Enclave Instructions and Protected Rings:
The enclave instructions available with SGX are divided under two protections rings.
1. Ring 0 Instructions:
ECREATE, EADD and EINIT are used for EPC management thus executed by privileged software such as OS and VMM
1. Ring 3 Instructions:
EENTER, EEXIT, EGETKEY, EREPORT and ERESUME are used by the user space software to execute functionality within or between enclaves.
Overview of an SGX Enclave Life Cycle:
An enclave’s life cycle is deeply intertwined with resource management, specifically the allocation of EPC pages. Therefore, the instructions that transition between different life cycle states can only be executed by the system software.
Enclave Creation Process
Loads enclave binary into the EPC and establishes identity.
ECREATE
- Finds a free EPC page and makes it the Enclaves SECS
- Stores enclave initial attributes (mode of operation, debug, etc.)
EADD
- Commits information (REG) or TCS as a new enclave EPC entry pages (4KB at a time).
- Creates and updates associated EPCM entry.
EEXTEND
- Measures 256Byte of info. Into CryptoLog (thus runs 16 times to measure one page).
EINIT – ensures only measured code has enclave access!
- Gets as input: SIGSTRUCT, EINITTOKEN
- EINITTOKEN is generated using this CPU's Launch key, and contains: MRENCLAVE, MRSIGNER & ATTRIBUTES. (These values must match the corresponding values in the SECS)
- Verifies and creates enclave identities:
- Finalizes measurements for MRENCLAVE.
- Validates SIGSTRUCT with enclosed public key
- Uses ISV’s signed SIGSTRUCT to validate MESIGNER and MRENCALVE.
- Checks that no Intel-only bits are set in SIGSTRUCT.ATTRIBUTES unless SIGSTRUCT was signed by Intel.
- Stores these and some other attributes in enclave’s SECS.
- Enables enclave entry (mark as ready to be used)
Enclave Entry and Exit execution
CPU flow control under enclave mode
EENTER
- Gets enclave TCS address as parameter
- Verifies validity of enclave entry point
- Check that TCS is not busy and marked it as “BUSY”.
- Clears any translation remainder in cache (TLS)
- Sets Asynchronous Exit Pointer (AEP) parameter
- Change CPU mode of operation to “enclave mode”.
- If not debug, set HW so the enclave appears as a single instruction.
ERESUME
- AEP will mostly hold the ERESUME inst. address.
EEXIT
- Clear any translation remainder in cache (TLB)
- TCS is marked as “FREE”
- Jumps out of enclave flow back to OS instruction address (stored in RBX)
- Enclave developer is responsible for clearing registers state.
Making use of SGX Enclave
Independent software vendor (ISV) enclave development process.
- Identify sensitive parts of application.
- Move sensitive logic to enclave project and compile.
- Multi-threaded enclave is supported by creating multiple TCS EPC entries.
- Create accompanying enclave certificate (SIGSTRUCT)
- Measure enclave content using SHA-256
- Specify attributes
- Set ISV information like Product ID, Security version number – SVN
- Sign with ISV private key.
- An enclave is in the clear before instantiation
- Sections of code and data could be encrypted, but their decryption key can’t be pre-installed.
- Secrets come from outside the enclave after it satisfies 3rd part’s trust.
- Subsequent runs use provisioned secrets again.
For more such intel Modern Code and tools from Intel, please visit the Intel® Modern Code
Source:https://software.intel.com/en-us/blogs/2016/12/20/overview-of-an-intel-software-guard-extensions-enclave-life-cycle




