Overview: Intel Device Protection Technology for Android for Intel devices
Here's an introduction and overview of Intel Device Protection Technology for Android. This overview explains how you can use the platform to protect against data leakage and protect you device and content from security threats on Android
Current Android Platform Environment
Recent industry reports have indicated that over 70% of tablets and smartphones worldwide use the Android OS. However, due to Android's open platform, the OS does not provide sufficient protection from malicious apps or Trojans. Additionally, many companies concerned about the increased popularity of bring-your-own-device (BYOD) programs have prohibited employee use of Android-based devices that aren't compatible with the company's security requirements. The following are cited as primary concerns for Android open platform OS:
- Insufficient protection from malicious apps and Trojans
- Incomplete device security/management APIs
- RootKit exposure
- Unauthorized boot-loaders
At CES 2014, Intel CEO Brian Krzanich announced how Intel plans to address these growing concerns by offering expanded security capabilities with Intel Device Protection Technology for Intel architecture-based mobile devices running the Android OS.
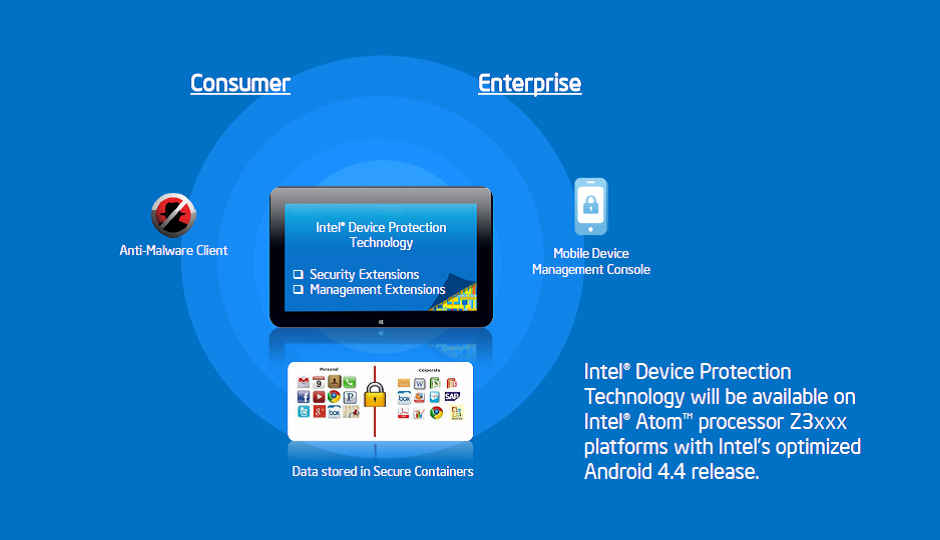
Intel Device Protection Technology offers users new security capabilities to help proactively secure Android mobile devices and block malware. Enterprise user-managed devices and BYODs will also benefit from hardware and software-enhanced security capabilities that provide IT increased levels of control and effectively separate personal and corporate applications and data. This combination of features helps protect against data leakage while safeguarding personal content on the device.
Key Points of Intel's Enhanced Security Capabilities
- Intel Device Protection Technology will be integrated into Intel architecture-based Android platforms, providing benefits to enterprise users and consumers.
-
Intel is providing a set of software extensions on Intel-enhanced Android platforms that, when combined with a product such as McAfee Mobile Security* (MMS), delivers proactive protection for mobile devices. The extensions provide dynamic whitelisting, efficient malware scans, URL/web filtering, and contextual permission management capabilities. Additionally, it includes proactive scanning of applications and web sites to intercept malware before it's installed on a mobile device. Faster and more efficient routine scans of the device are optimized, reducing impact on the processor and battery life of the device.
- Manageability Extensions help enable enhanced mobile device management (eMDM) for enterprise IT via software-based extensions to the Android framework and kernel. eMDM also is supported by Intel's security engine that includes hardening for encryption and key protection. Manageability Extensions provide MDM vendors the ability to securely lock down Android devices for better manageability.
- Enterprise-managed mobile devices running an Intel-enhanced version of Android will benefit from hardware and software enhanced security capabilities that provide IT increased levels of control and effectively separate corporate and personal applications and data, thus protecting against data leakage while safeguarding personal content on the device.
- For consumers, Intel Device Protection Technology will enable proactive malware protection, separation of personal and corporate data for BYODs, with native Android apps to enhance the user experience.
How Intel Device Protection Technology Works
Intel's goal is to provide a robust set of security features. Intel's security extensions will be preloaded on IA-based devices and enable all OEMs to provide enterprise-ready solutions more quickly. These extensions will ship with IA-based devices and can be leveraged with enabled MDM vendor console solutions. Intel is working with MDM vendors to enable a broad set of solution possibilities.
Intel actively works with Google to enhance the entire Android stack for end users. Intel is typically the leading provider (outside of Google) to contribute code to the Android Open Source Project and intends to continue transitioning as Google evolves its native support for such enterprise capabilities.
There are several approaches to delivering these solutions. Intel's solution is deeply integrated in its software stack and extends its capabilities to deliver a trusted BYOD solution. Its deep integration has been in full compliance to preserve Android compatibility, and Intel has worked hard to limit changes to the Android OS.
Intel will be making its APIs available more broadly to security software vendors. By implementing the extensions in the core platform, trusted vendors have the ability to develop solutions that better manage the devices and intercept malware.
Enterprise Manageability
The Secure Container and Extended Mobile Device Management capabilities enable IT departments to manage their assets without infringing on a consumer's personal experience or data. Corporate IT managers can encapsulate any app from any app store and lock down its contents securely. In most cases, the IT administrator will determine which apps may be installed in a container and would likely create an approved list of applications for that purpose. Applications may be installed from a corporate store or from a public application store, like Google Play, if the administrator enables that functionality.
Personal photos and emails can exist outside the container so that if the IT organization needs to lock or remove the corporate container, it will not impact a customer's personal content.
For example, in order to protect enterprise data, some solutions require removing all data from the device to ensure sensitive information is protected. Suppose a corporate container is locked or deleted by IT. By utilizing a container, IT can segment the information so that removing one container does not impact the information outside of the container. Even if a container is wiped or locked, a user would still have access to the device and personal data stored outside of the container.
The containers also offer capabilities to protect corporate information from data leakage and personal data on BYODs from being mingled with work data on a managed device. When data is stored in a container, it is only accessible to users who log in to the container and cannot be copied electronically from the container.
These security extensions can also be utilized with enabled MDM vendor console solutions. Intel is working with the vendors in the MDM ecosystem to support these enhancements in its consoles. For new MDM functionality in eMDM, Intel's solution extends the standard Android Device Management APIs by providing more granular application management, device inventory, and configuration; adding network configuration controls; and setting policies for telephone expense management. We have implemented near-native solutions that do not require cloud wrapping of applications to prevent enterprise data leakage. This offers end users the flexibility to download apps from any app store and offers enterprises scalability in managing such open Android devices while still securing the exposure of enterprise data. These enhancements give IT managers more tools to efficiently and effectively manage devices.
Separation of Personal and Corporate Data
Consumers benefit from this technology and from software and services utilizing the capabilities of the extensions. The ability to proactively protect devices through Security Extensions-enabled products is available to all end users. However, to utilize the manageability and container functionality, it would require a Mobile Device Management tool, which is normally provided by corporations.
There are also benefits to an end user if a security service is not pre-installed. By including the extensions, people can still take advantage of enhanced security solutions when they come to market. Trusted partner security solutions could be downloaded from application stores, such as Google Play, and utilize the APIs once the chosen security solution is installed on the device.
2014 Availability
Intel expects to bring these enhanced security capabilities to market in the first half of 2014, starting with a new version of McAfee Mobile Security (MMS v3.2) that provides increased security benefits for consumers. Intel Device Protection Technology will also be available on Intel® Atom� processor Z3xxx platforms (Bay Trail) with the Intel-optimized Android 4.4 release. Look for additional information from Intel at Mobile World Congress and RSA in February 2014.
For more such Android resources and tools from Intel, please visit the Intel® Developer Zone
Source: https://software.intel.com/en-us/android/articles/intel-device-protection-technology-for-android-on-intel-architecture







