IoT Security Made Simple with Wind River Linux

A security breach of an Internet of Things (IoT) device can lead to serious hazards. The always-on, always-connected nature of IoT devices exposes a larger threat surface that requires stronger security capabilities. That’s why integrating security into these devices is critical not just during the build phase but throughout the product life cycle.
When building IoT products, your priority as a developer is to make the development life cycle fast, simple, and cost-effective. This approach may not be feasible, however, when you use an embedded Linux platform if the onus of addressing individual security vulnerabilities remains on you. You need a platform that supports robust security integration, monitoring, and upgrades throughout the product life cycle.
The open source collaboration called Yocto Project* has simplified IoT embedded Linux life-cycle support with a broad set of user-space packages; encapsulation and separation of software and middleware; a standardized cross-build methodology for kernel, packages, patches, and other standardized tools; and infrastructure. Wind River, a leading contributor to the Yocto Project, developed its embedded Linux platform by integrating the Yocto* 2.0 open source framework. Features such as built-in certifiable security capability, portability across hardware platforms, and life-cycle maintenance support make this Wind River Linux ideal for simplifying your overall development life cycle.
A Smart Platform on Which to Build Smart Appliances
Wind River Linux supports a wide range of IoT devices in terms of size, architecture, and industry. It gives you access to vital security as well as faster build and deployment capabilities, with key features such as:
- Off-the-Shelf Run Times: Preconfigured profiles for various device types, sizes, latency, and power management let you jump-start device development.
- Minimal Installation Provisions: Begin with a smaller initial download, and incrementally download packages as you need them during the build process.
- Project-Specific, Tailored Environment: The certified binary distribution allows you to customize your middleware development environment. Using this customized environment, you can develop and integrate security, connectivity, rich networking options, and cloud management easily. Certified binary feeds let you directly integrate updates and security fixes.
- Advanced Built-In Security: Secured boot authenticates all stages of the boot process. A secure runtime loader prevents code tampering and unauthorized execution, and an advanced user management system protects against unauthorized access and allows the use and enforcement of user-based policies and permissions. Secure network communications are accomplished through Security protocols such as Wind River SSL (Secure Sockets Layer), Wind River SSH (Secure Shell), Wind River IPsec (IP security), and Wind River IKE (Internet Key Exchange).
- Life-Cycle Support: Using an innovative patch management technology, Wind River delivers bug and security fixes with predictability.
- Automatic Updates: Updated binaries are automatically detected and downloaded.
- Portability: Support for a broad spectrum of silicon architectures and board support packages, including Freescale, Intel, LSI, Texas Instruments, and Xilinx platforms adds flexibility to your security implementations.
- Reduced Build Time: Fifteen-second quick boot, rapid installation, updates without the need for extra compilation and reboot, and centralized cloud orchestration access help reduce overall development time.
- Development Tools: Wind River Workbench and Wind River Simics* are included with the platform. The Workbench integrated development environment allows you to configure, analyze, debug, and optimize your system. With Simics, you can accelerate every phase of your development life cycle by extensively using simulations, reducing cost and the risks of shipping late or sacrificing quality.
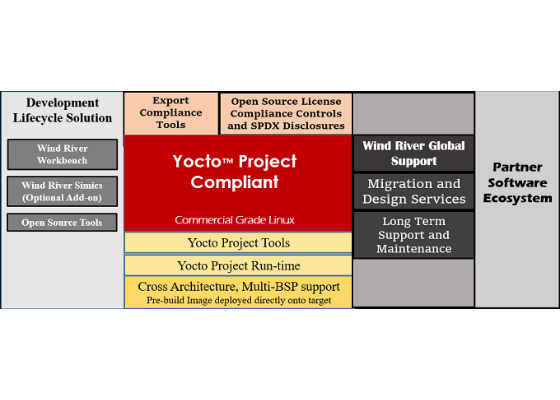
Figure 1 shows the architecture of Wind River Linux 8.
Figure 1. Wind River Linux 8 Architecture
Wind River Linux is interoperable with other open source projects, such as Toaster and Eclipse*, which can reduce the learning curve for new developers. With Wind River, you can use a simple, common framework to manage all your projects.
Build Secure Devices with Wind River* Linux*
With an increasing number of connected devices, security threats for Linux-based systems are on the rise. Threats include unauthorized access, data and device destruction, tampering with functionality, information disclosure, information modification, and denial-of-service attacks. Wind River Linux comes with Security Profile, a commercial off-the-shelf product that has the features necessary to fight these threats. Security Profile is in compliance with the Common Criteria scheme, an International Organization for Standardization/International Electrotechnical Commission 15408 standard for cybersecurity certification.
Because of increased cybersecurity concerns with connected products, the Common Criteria scheme, mostly used in regulated industries, have now expanded to other industries, as well. As a result, embedded software development should factor in these compliance criteria. Use case–specific security requirements in the Common Criteria scheme are documented using Protection Profiles and used for evaluation (with various Evaluation Assurance Levels) and certification.
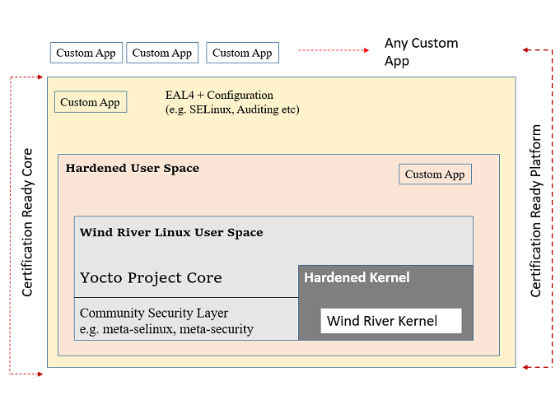
Certification of new products as compliant with these requirements can be both costly and time consuming. Wind River Linux Security Profile simplifies this process (Figure 2) by enabling multiple Protection Profiles feature templates, including:
- Operating System Protection Profile (OSPP) and Validation Tools;
- General-Purpose OSPP;
- Labelled Security Protection Profile; and
- Role-Based Access Control Protection Profile.
Figure 2. Security Profile for Wind River Linux architecture
The Security Profile architecture includes a security-focused, hardened kernel that uses PaX to implement least-privilege protections for memory pages. This approach protects systems from security exploits such as buffer overflows and return-to-libc attacks. Features such as enhanced Address Space Layout Randomization, memory corruption–based exploit prevention, memory sanitizing, and path-based security policy with zero run time memory allocation harden your product at no extra cost.
Secure-core and platform options built into the secure user space prevent run time buffer overflow. The operating system also includes a suite of tools with which you can lock down, monitor, and audit a system, all of which give you greater insights and control for maintenance and troubleshooting. The Security Profile also supports multitier security with stacked Linux Security Modules. Trusted computing with root of trust is built in.
Constant scrutiny over all software update releases is critical for always-on devices. Continuous regression tests and bug-fix patch releases for such devices can add significant time and cost to your development life cycle, but when you use Wind River Linux, Wind River’s team of specialists handle these tasks for you.
The Wind River Linux security response team monitors 24×7 security threats. The team provides hot patches to the market’s best known threats with-24-hour response times. You get security mitigation, detailed system monitoring, forensics, and zero-day protection support from an experienced, highly reliable team. In the long term, this support can save you significant time, money, and hassle compared to free Linux options.
Ship Faster, With Reduced Overhead and Simplified Workflow
As the embedded Linux footprint continues to expand in the IoT space, conformance to stronger security requirements is no longer optional. Today, security readiness is mandatory not just for regulated markets like aerospace and defense but in all commercial verticals. When you build secure IoT products, efficient handling of security compliance–related overhead is critical for reducing cost and meeting sensitive deadlines.
Wind River Linux as a commercial development platform provides you with a support team that understands your application, your hardware, and your unique environment, allowing you to stay focused on critical applications and product-specific features while the Wind River team of experts supports your Linux platform tools and security infrastructure.
Security Profile simplifies the Common Criteria scheme–based security certification for devices developed using preintegrated Protection Profiles. The feature guides you through the certification process with its Evaluation Configuration guide and documentation.
As security requirements harden, using commercial embedded platform such as Wind River Linux helps you simplify your workflow to efficiently build smart, secure, and resilient connected products that last for years.
For more such intel IoT resources and tools from Intel, please visit the Intel® Developer Zone
Source: https://software.intel.com/en-us/articles/iot-security-made-simple-with-wind-river-linux